Table of Contents
- Introduction
- Editor’s Choice
- Identity and Access Management Market Statistics Overview
- Security Incidents Driving the Demand for IAM
- Factors Organizations are Evaluating an (IAM) Solution
- Main Tools Integrated Within Companies’ IAM System
- Company Preferences for IAM Tools
- Cybersecurity and IAM Spending
- Recent Developments
- Conclusion
- FAQs
Introduction
Identity and Access Management Statistics: Identity and Access Management (IAM) is vital for cybersecurity. Ensuring control over who can access a company’s digital assets.
IAM confirms user identities, authorizes or restricts access, and oversees user accounts throughout their existence. It has gained significance due to rising digital complexities and security concerns, used across industries like finance, healthcare, and tech.
Cloud-based solutions and biometric authentication are increasingly common. IAM adheres to data protection rules and holds promise in the future with biometrics and AI-based access controls, safeguarding digital assets effectively.
Editor’s Choice
- The global Identity and Access Management (IAM) market is experiencing robust growth at a CAGR of 13.7%, with a clear upward trajectory in revenue over the coming years.
- In 2022, the market generated approximately USD 14.7 billion in revenue.
- Provisioning, responsible for managing user access and privileges, accounted for USD 4.3 billion in revenue, while Multifactor Authentication. A vital aspect of enhancing security through multiple authentication methods contributed USD 3.1 billion.
- As of the latest data, the majority of IAM solutions are deployed on-premise, comprising a substantial market share of 58%.
- Among the main ways cybercriminals infiltrate organizations, stolen credentials, and phishing stand out as two of the top three methods.
- Integration compatibility stands out as a top priority, with a substantial 72% of organizations giving it paramount importance.
- In 2022, the most widely adopted tool by companies worldwide was Security Information and Event Management (SIEM).
Identity and Access Management Market Statistics Overview
Global Identity and Access Management Market Size Statistics
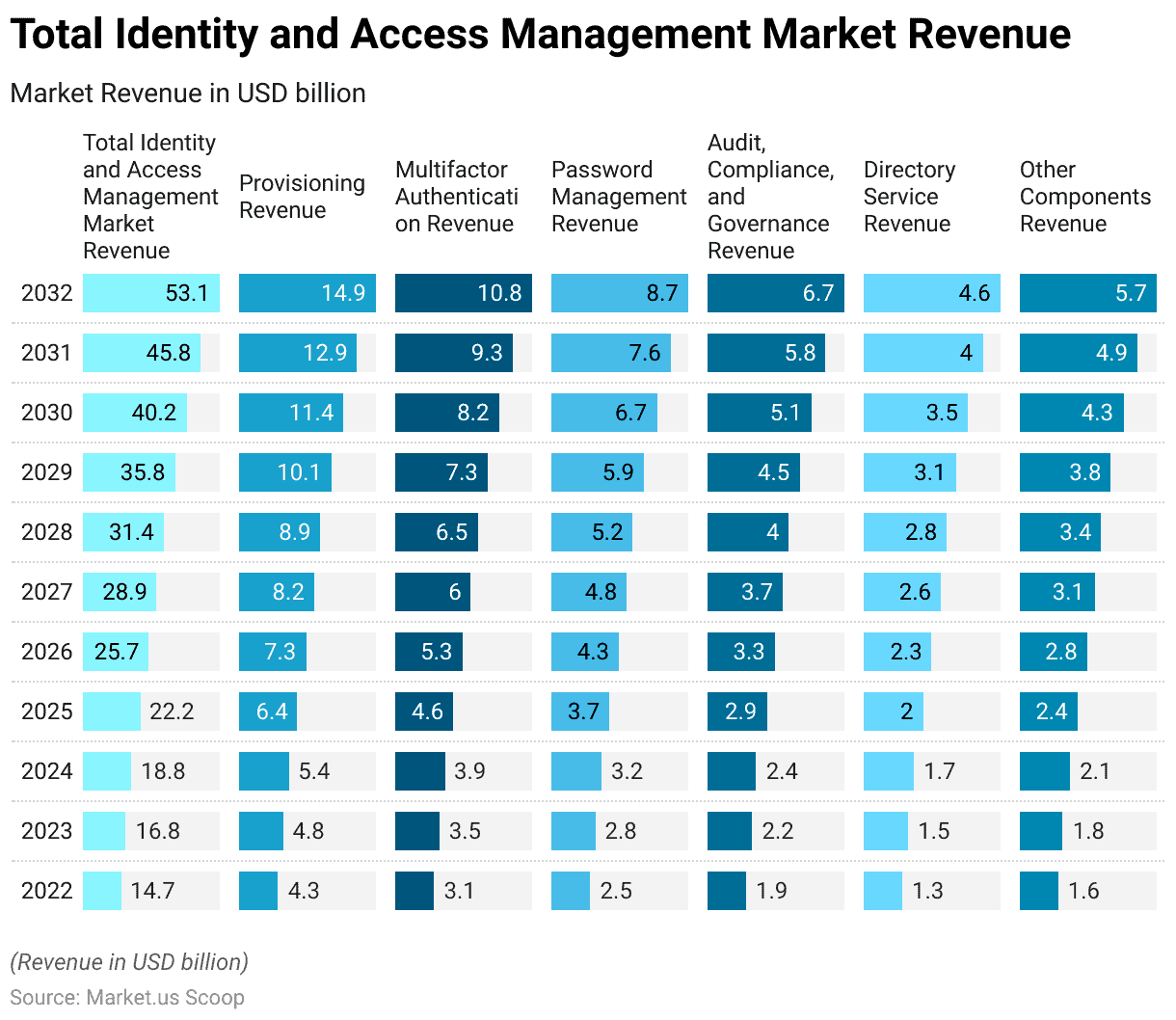
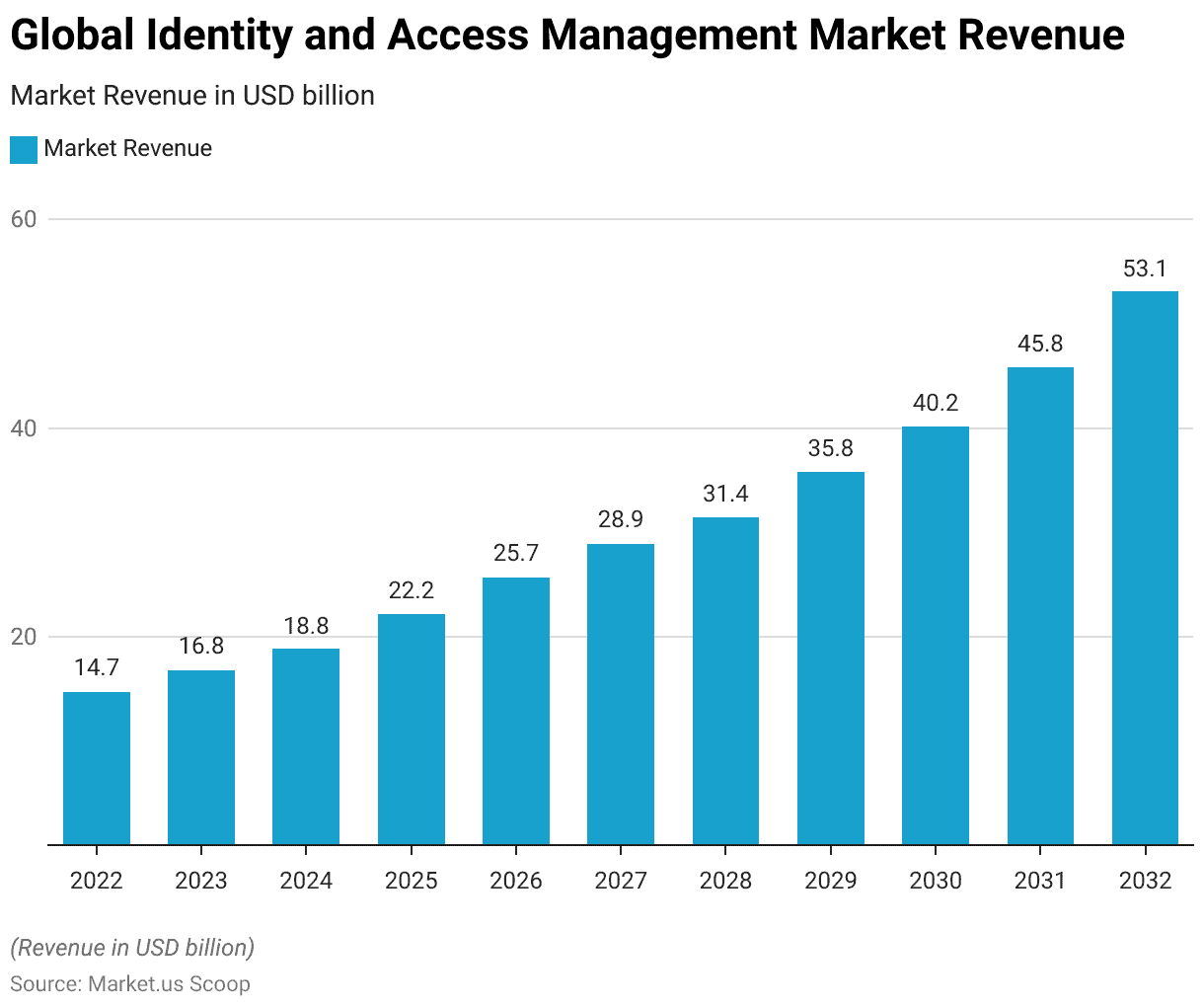
- The global Identity and Access Management (IAM) market is experiencing robust growth at a CAGR of 13.7%, with a clear upward trajectory in revenue over the coming years.
- In 2022, the market generated approximately USD 14.7 billion in revenue, marking the starting point of this upward trend.
- The subsequent years are projected to witness steady expansion. With revenues reaching USD 16.8 billion in 2023 and USD 18.8 billion in 2024.
- As we look ahead to the forecast period, the IAM market is expected to demonstrate even more substantial growth. With revenue estimates climbing to USD 22.2 billion in 2025, USD 25.7 billion in 2026, and USD 28.9 billion in 2027.
- The momentum continues, with projected revenues of USD 31.4 billion in 2028, USD 35.8 billion in 2029, and USD 40.2 billion in 2030.
- The growth trend remains strong, reaching USD 45.8 billion in 2031 and USD 53.1 billion in 2032.
- This impressive trajectory underscores the increasing importance of IAM solutions in today’s digital landscape. Organizations recognize the critical need for secure access and identity management in an evolving technological environment.
(Source: Market.us)
Identity and Access Management Market Share – By Component Statistics
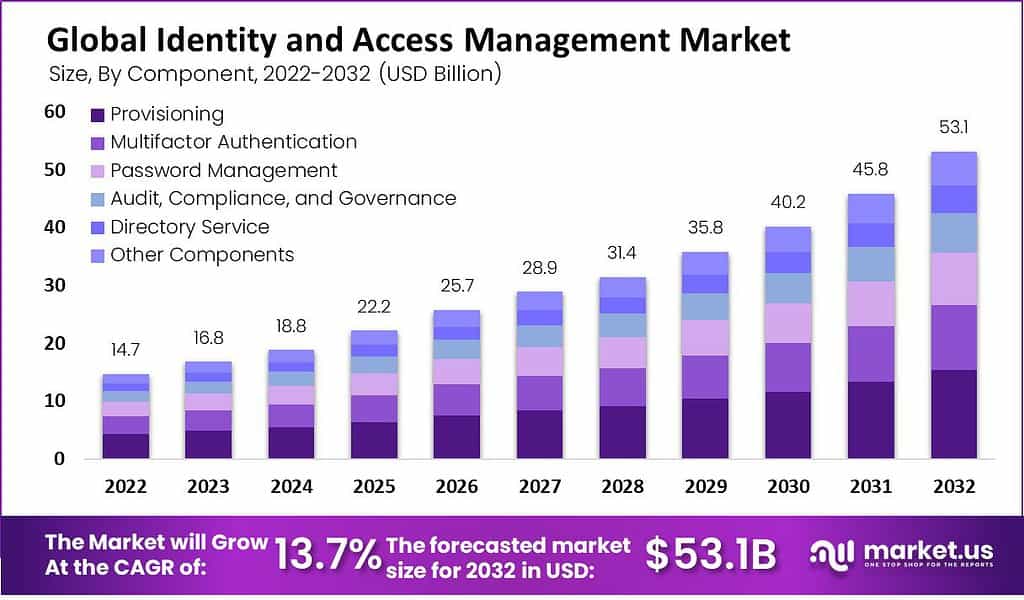
- The Global Identity and Access Management (IAM) market exhibits a comprehensive breakdown by component, revealing a clear picture of its revenue distribution over the years.
- In 2022, the IAM market initiated its journey with a total revenue of USD 14.7 billion. Within this landscape, several critical components played distinct roles.
- Provisioning, responsible for managing user access and privileges. Accounted for USD 4.3 billion in revenue, while Multifactor Authentication, a vital aspect of enhancing security through multiple authentication methods, contributed USD 3.1 billion.
- Password Management, essential for safeguarding sensitive information, generated USD 2.5 billion in revenue.
- Audit, Compliance, and Governance, crucial for regulatory adherence and security control, added USD 1.9 billion. While Directory Service, responsible for organizing user data and resources, accounted for USD 1.3 billion.
- Other Components, encompassing various IAM-related services and solutions, contributed USD 1.6 billion to the market.
- As we progress through the forecasted years, the IAM market is set to experience significant growth, culminating in a substantial revenue of USD 53.1 billion by 2032.
- This growth trajectory underscores the increasing importance of IAM solutions across diverse industries. Highlighting the critical role played by these components in ensuring secure identity and access management within today’s rapidly evolving digital landscape.
(Source: Market.us)
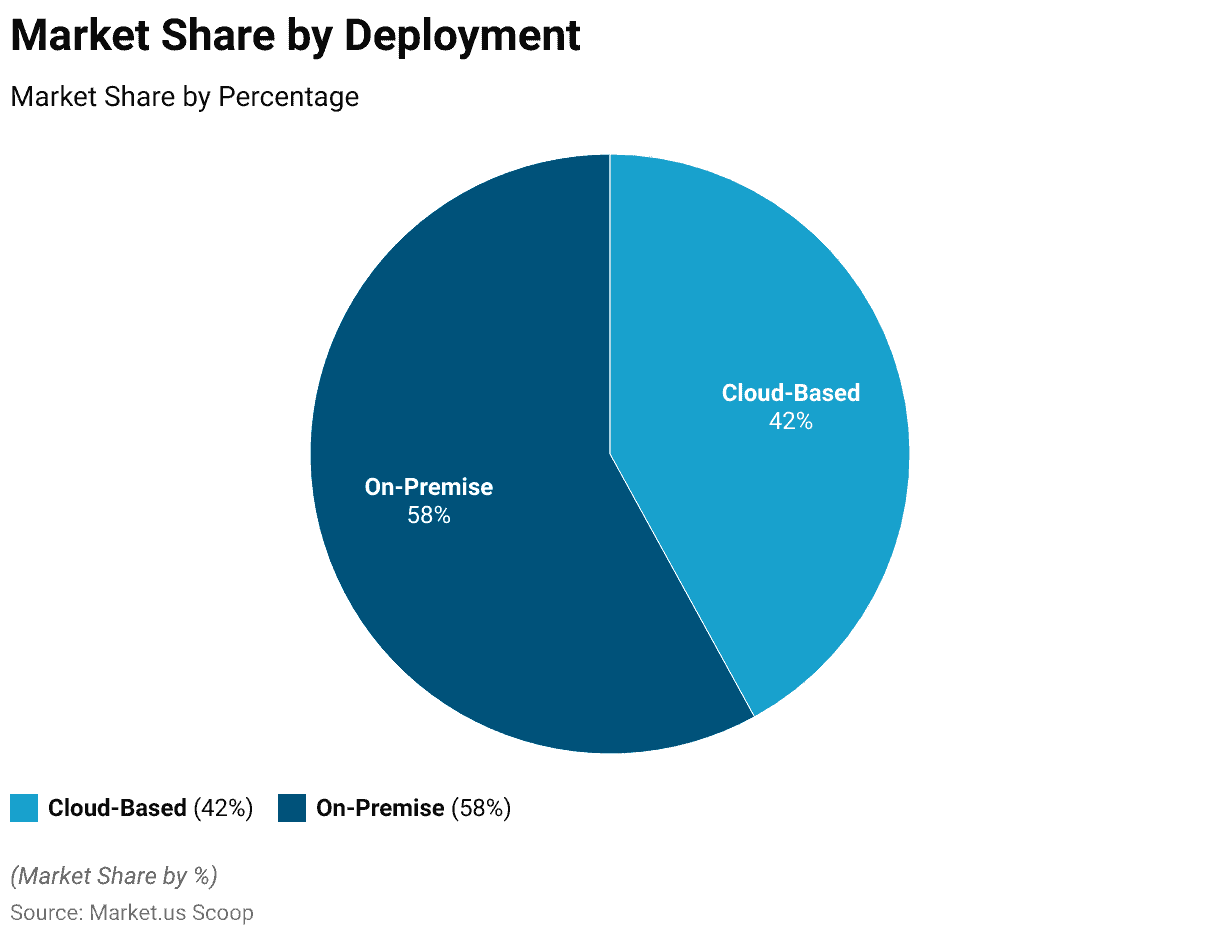
Global Identity and Access Management Market Share – By Deployment Statistics
- The Global Identity and Access Management (IAM) market exhibits a significant division in terms of deployment modes.
- As of the latest data, the majority of IAM solutions are deployed on-premise, comprising a substantial market share of 58%.
- This indicates a prevalent preference for organizations to maintain IAM systems within their infrastructure. Often driven by factors such as security, control, and legacy systems integration.
- In contrast, the cloud-based deployment mode has steadily gained traction, accounting for 42% of the market share.
- This shift towards cloud-based IAM solutions reflects a growing recognition of the scalability, flexibility, and cost-effectiveness offered by cloud technology in managing identities and access. Aligning with the evolving needs of modern businesses seeking efficient and adaptable solutions for secure identity management.
(Source: Market.us)
Security Incidents Driving the Demand for IAM
- Among the main ways cybercriminals infiltrate organizations, stolen credentials, and phishing stand out as two of the top three methods.
- Notably, in 74% of all security breaches, human actions play a significant role. This involvement includes misusing privileges, and employing stolen login information. Employing social engineering tactics, or making errors, and it’s worth noting that three out of these four approaches are directly tied to user identities.
- This trend is expected to persist, with a continued surge in password-related attacks. Notably, this year has witnessed a more than tenfold rise in attempted password attacks compared to the same period last year.
- Additionally, according to additional research by Crowdstrike, there has been a 112% year-on-year surge in advertisements for access-broker services in the criminal underground, such as the dark web.
- This increase underscores the fact that threat actors are intensifying their efforts in credential-based attacks.
- Data breaches have taken a toll on nearly 90% of financial institutions, and a significant 60% of these incidents have involved identity theft.
- Studies show that over 80% of data breaches occur due to the usage of stolen, default, or feeble passwords.
- By deploying Identity and Access Management (IAM) systems that enforce top-tier credential management practices. Organizations can significantly mitigate the risk of users employing vulnerable or default passwords, essentially eliminating this threat.
- In the past year, the two most common ways breaches occurred were through phishing attacks. Accounting for 16% of breaches, and the use of stolen or compromised credentials is responsible for 15% of all breaches.
(Source: Verizon, Microsoft, Crowdstrike, Imperva, IBM)
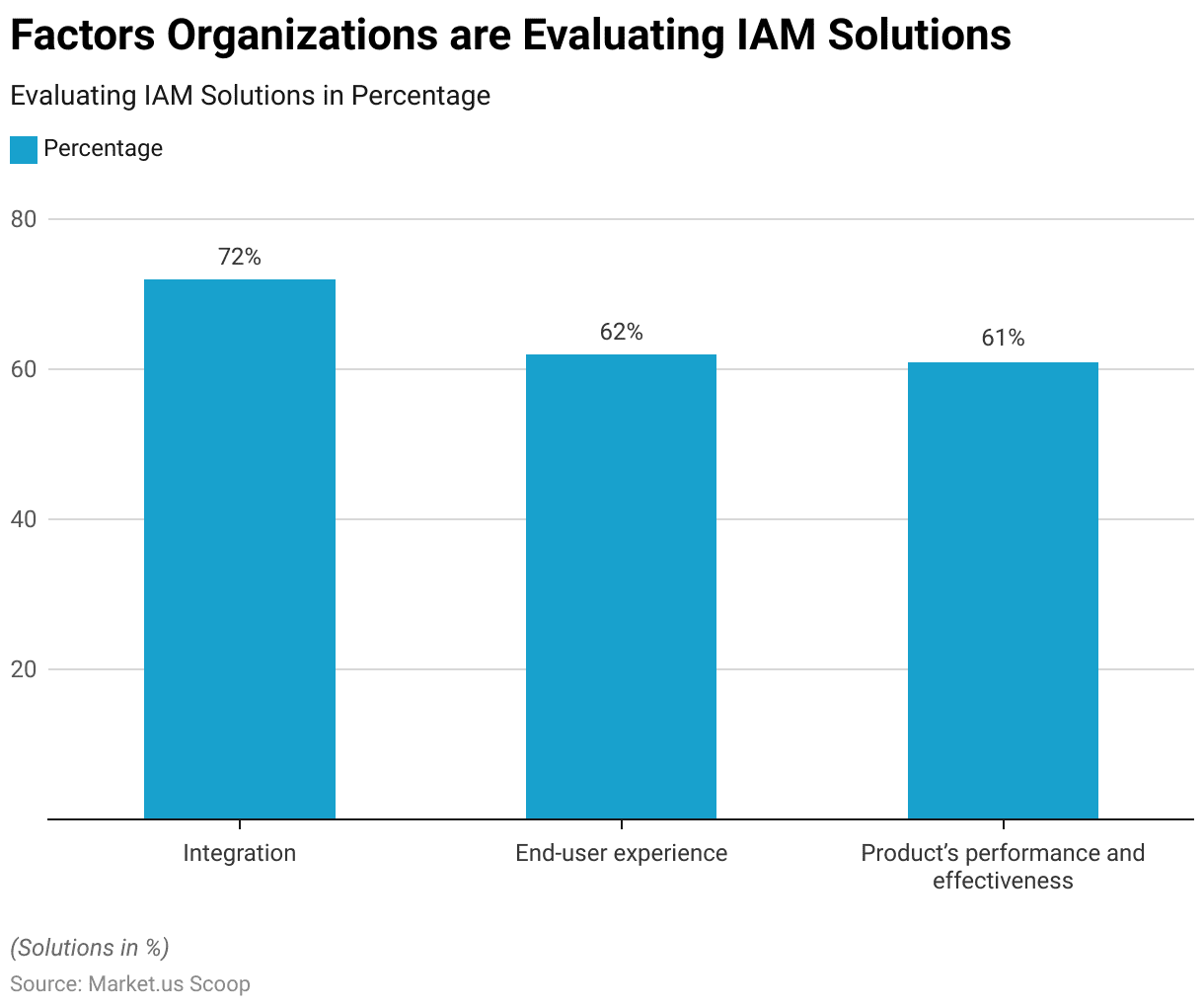
Factors Organizations are Evaluating an (IAM) Solution
- Organizations are meticulously evaluating Identity and Access Management (IAM) solutions, considering several critical factors.
- Integration compatibility stands out as a top priority, with a substantial 72% of organizations giving it paramount importance.
- Ensuring a seamless integration of IAM systems into their existing infrastructure is crucial. The end-user experience follows closely, with 62% of organizations emphasizing the need for user-friendly and efficient IAM solutions.
- Additionally, the product’s performance and effectiveness weigh significantly, with 61% of organizations scrutinizing IAM solutions. To ensure they meet the high standards required for safeguarding digital assets and providing robust access control.
- These factors collectively underline the meticulous approach organizations take when selecting IAM solutions to enhance their cybersecurity and user experiences.
(Source: Expert insights)
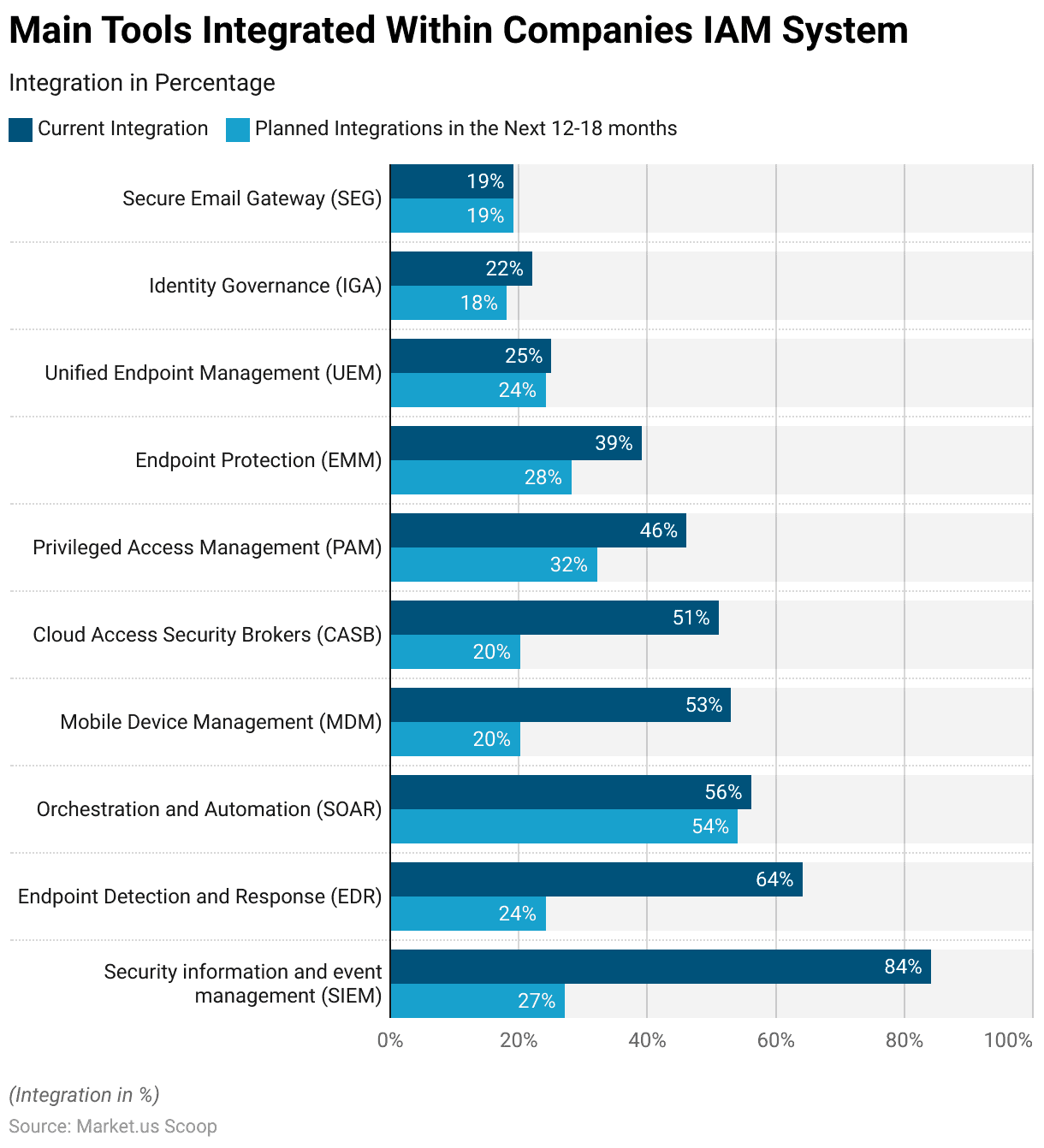
Main Tools Integrated Within Companies’ IAM System
- In the realm of Identity and Access Management (IAM) systems worldwide in 2022, several key tools were integrated within companies to bolster security and access control.
- Leading the pack, Security Information and Event Management (SIEM) was the most widely integrated tool, with an impressive 84% adoption rate.
- This tool plays a vital role in proactively detecting and responding to security incidents.
- Endpoint Detection and Response (EDR) followed closely, integrated by 64% of organizations, enhancing their ability to monitor and secure endpoints.
- Orchestration and Automation (SOAR) tools were also prevalent, with 56% integration, with even more organizations planning to adopt them in the next 12-18 months, highlighting their importance.
- Other tools, such as Mobile Device Management (MDM), Cloud Access Security Brokers (CASB), Privileged Access Management (PAM), and more. These were integrated at varying levels, indicating the comprehensive approach organizations are taking to fortify their IAM systems and security posture.
(Source: Statista)
Company Preferences for IAM Tools
- Identity and Access Management (IAM) tools have three primary functions: identification, authentication, and authorization.
- In 2022, the most widely adopted tool by companies worldwide was Security Information and Event Management (SIEM).
- SIEM plays a crucial role in proactively identifying and responding to security threats by combining security software and services with information and event management. Organizations typically manage IAM tools internally, using cloud-native assessment tools such as AWS IAM Access Analyzer.
- Despite the strong recommendation for automated IAM systems, around 38% of survey respondents indicated that their organizations still manually controlled IAM policy statements and configurations.
- Additionally, to align with a Zero Trust security framework, companies must integrate various tools into their IAM systems, recognizing the pivotal role IAM plays in this approach.
- By the close of 2022, a majority of organizations had already implemented single sign-on (SSO) and multi-factor authentication (MFA) methods for their employees within their IAM systems.
(Source: Statista)
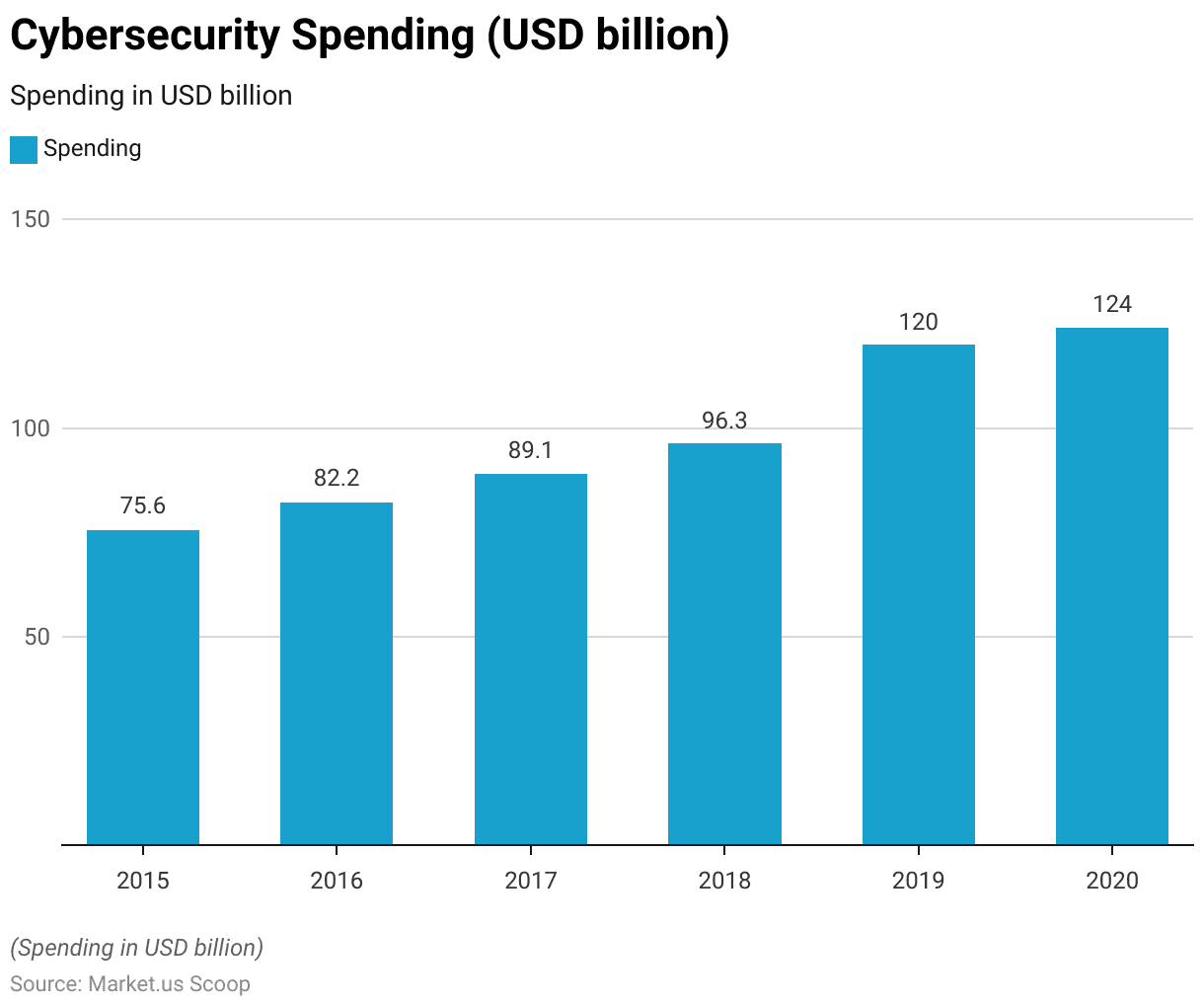
Cybersecurity and IAM Spending
- Cybersecurity spending has exhibited consistent growth over the past six years.
- In 2015, global expenditure on cybersecurity stood at USD 75.6 billion, marking the beginning of this upward trajectory.
- The following years witnessed a steady increase, with 2016 reaching USD 82.2 billion and 2017 reaching USD 89.1 billion.
- By 2018, organizations worldwide allocated USD 96.3 billion to bolster their cybersecurity measures.
- Notably, in 2019, there was a substantial leap in spending, reaching USD 120 billion, indicative of the growing recognition of the importance of cybersecurity.
- This commitment to security persisted in 2020, with global cybersecurity spending reaching USD 124 billion. Underscoring the ongoing dedication to safeguarding digital assets and data in an increasingly connected world.
(Source: Statista)
Recent Developments
Acquisitions and Mergers:
- Okta acquires Auth0: In 2023, Okta, a leading identity management company, completed its acquisition of Auth0 for $6.5 billion. This acquisition strengthens Okta’s position in the IAM market by integrating Auth0’s developer-centric identity solutions, targeting businesses looking for customized identity management tools.
- Thales acquires OneWelcome: In 2023, Thales, a global leader in cybersecurity, acquired OneWelcome, a European provider of IAM solutions, for $100 million. This acquisition enhances Thales’ ability to offer secure digital identity management for customers across Europe, particularly in the banking and government sectors.
New Product Launches:
- Microsoft introduces Entra for Identity and Access Management: In 2024, Microsoft launched Microsoft Entra, a unified IAM platform that integrates multi-cloud and on-premise security management. The platform focuses on managing digital identities, enabling secure access for hybrid work environments and cloud services.
- IBM releases AI-powered IAM: In early 2024, IBM launched a new AI-powered IAM solution that automates identity lifecycle management and uses machine learning to detect and mitigate potential security threats. This product is designed for enterprises looking for enhanced security features driven by AI.
Funding:
- Saviynt secures $200 million in funding: In 2023, Saviynt, a cloud-based identity management company, raised $200 million in a funding round led by venture capital firms. The funds are targeted at scaling their Identity Governance and Administration (IGA) platform and expanding their global operations.
- ForgeRock raises $100 million: In early 2024, ForgeRock, an IAM provider, secured $100 million in funding to enhance its cloud-based IAM platform. The funds will be used to accelerate AI-driven identity management capabilities and improve customer security experience.
Technological Advancements:
- AI integration in IAM solutions: Artificial intelligence (AI) is being increasingly integrated into IAM platforms to enhance security and decision-making processes. By 2025, 50% of IAM platforms are expected to incorporate AI-driven analytics to detect anomalies, automate identity provisioning, and predict potential security breaches.
- Zero Trust Architecture adoption: Zero Trust is becoming the standard for IAM solutions. By 2026, over 60% of enterprises are projected to adopt Zero Trust frameworks within their IAM systems, focusing on securing access regardless of user location or device.
Conclusion
Identity and Access Management Statistics – Identity and Access Management (IAM) holds a critical role in contemporary cybersecurity.
Ensuring that solely authorized users or entities possess the right access to digital resources, thus diminishing the likelihood of data breaches.
The growing incorporation of IAM into other security tools signifies a holistic security strategy. Amid ever-changing cyber threats, IAM retains its crucial role in preserving digital assets.
Advancements in biometrics and access controls bode well for its future. In a global landscape where data security reigns supreme, IAM emerges as a fundamental cornerstone within cybersecurity strategies.
FAQs
IAM is a comprehensive approach to managing digital identities and controlling access to an organization’s systems, data, and applications. It involves verifying user identities, authorizing access, and managing user permissions.
IAM is essential for enhancing cybersecurity and data protection. It ensures that only authorized individuals or entities have access to sensitive resources, reducing the risk of data breaches and unauthorized access.
IAM typically includes three main components: identification (verifying user identities), authentication (confirming the user is who they claim to be), and authorization (granting or denying access based on user roles and permissions).
IAM improves security, enhances regulatory compliance, streamlines user access management, and reduces operational costs. It also simplifies password management and enhances user experiences.
Common IAM technologies include Single Sign-On (SSO), Multi-Factor Authentication (MFA), Role-Based Access Control (RBAC), and Privileged Access Management (PAM). IAM solutions are often offered by various vendors.


