Table of Contents
- Introduction
- Editor’s Choice
- Encryption Software Market Statistics
- Use of Enterprise-Wide Encryption Software Solutions Statistics
- Cost of Data Breach for Enterprise Software Statistics
- Identify and Contain a Data Breach By Average Time
- Average Time to Identify and Contain a Breach by Initial Attack Vector
- Businesses with Consistent Software Encryption Statistics
- Recent Developments:
- Conclusion
- FAQs
Introduction
Encryption Software Statistics: Encryption software is essential for protecting digital data, using cryptographic algorithms to turn readable information into a secured format to prevent unauthorized access.
It includes symmetric encryption, which uses one key for both encrypting and decrypting, ideal for handling vast amounts of data quickly, and asymmetric encryption, which uses a key pair for securing data exchanges and verifying user identities.
Its uses are widespread, from securing data and communications to ensuring the authenticity and integrity of information.
When choosing encryption software, factors like encryption strength, system performance impact, ease of use, and regulatory compliance are crucial.
Addressing challenges like secure key management and regulatory adherence is vital for maintaining effective data protection, highlighting the need for ongoing strategy adjustments to face new threats and technological changes.
Editor’s Choice
- The global encryption software market revenue is expected to reach USD 60.7 billion by 2033.
- Within this market, software revenue constitutes a significant portion, expected to grow from USD 9.9 billion in 2023 to USD 41.3 billion by 2033.
- Over the decade from 2012 to 2022, among various industries, the technology and software sector saw its adoption figures leap from 31% to a commanding 72%, showcasing its forefront position in encryption uptake.
- A notable uptick was observed in 2021, with the average total cost reaching 4.24 million USD, reflecting potential shifts in cybersecurity challenges and mitigation strategies across industries.
- 2021 saw a significant surge, with the average per-record cost reaching 161 USD, indicating potential shifts in data breach severity and associated costs, potentially influenced by evolving cybersecurity landscapes and regulatory frameworks.
- Notably, in 2021, there was a further increase in both identification and containment times, with breaches taking an average of 212 days to identify and 75 days to contain, potentially reflecting the evolving complexities and challenges in data breach detection and mitigation strategies.
- In 2015, 37% of businesses reported implementing an overall encryption plan or strategy consistently across their entire enterprise.

Encryption Software Market Statistics
Global Encryption Software Market Size Statistics
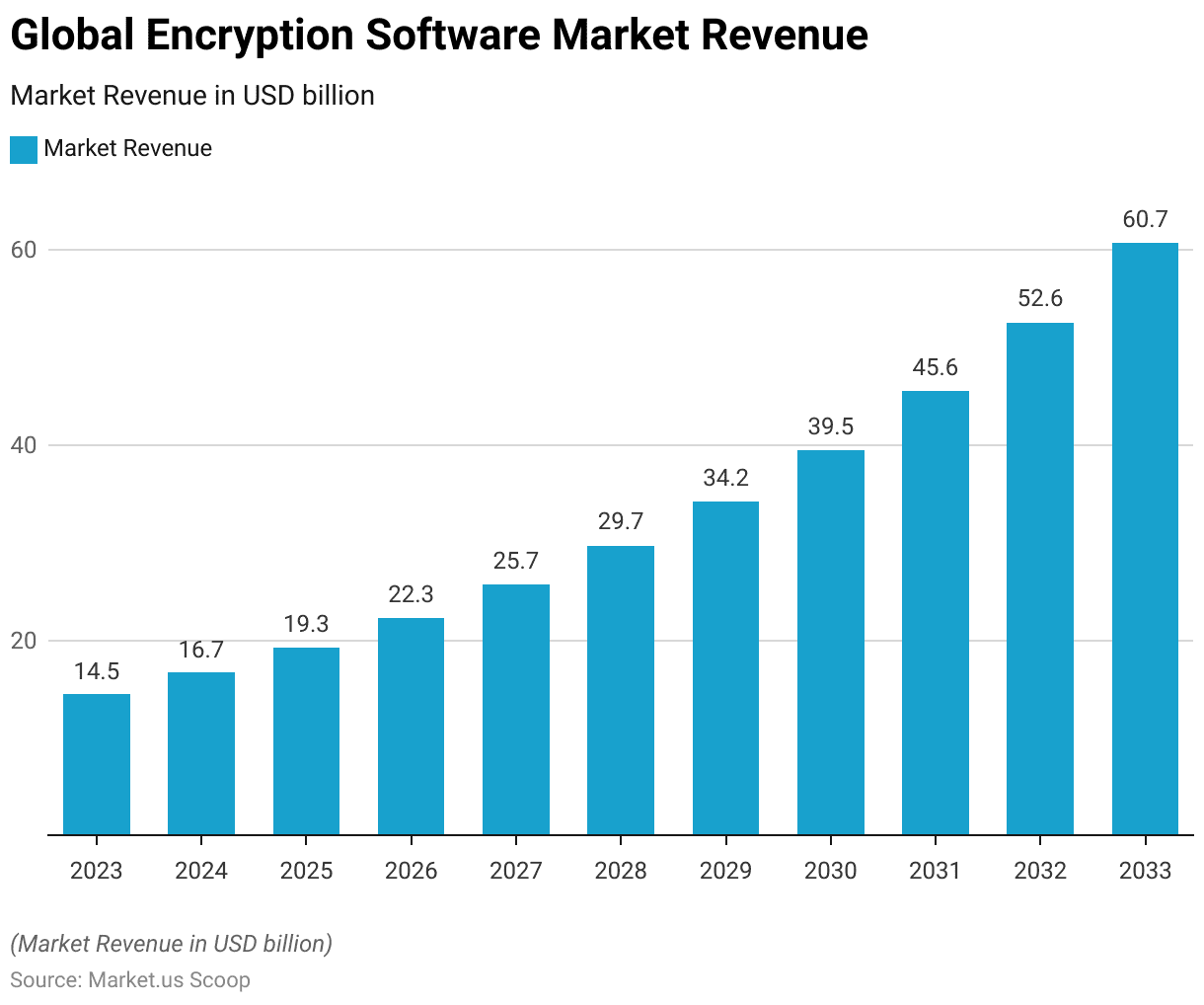
- The global encryption software market is projected to experience substantial growth over the next decade at a CAGR of 15.4%, with revenues forecasted to increase from USD 14.5 billion in 2023 to USD 60.7 billion by 2033.
- This upward trend highlights a compound annual growth rate, starting with USD 16.7 billion in 2024 and showing steady increases: USD 19.3 billion in 2025, USD 22.3 billion in 2026, and USD 25.7 billion by 2027.
- The market is expected to continue its expansion, reaching USD 29.7 billion in 2028, USD 34.2 billion in 2029, and USD 39.5 billion in 2030, before accelerating to USD 45.6 billion in 2031, USD 52.6 billion in 2032, and finally, USD 60.7 billion in 2033.
- This consistent growth underscores the escalating demand for encryption solutions driven by the global need to secure data against increasingly sophisticated cyber threats.
(Source: Market.us)
Global Encryption Software Market Size – By Component Statistics
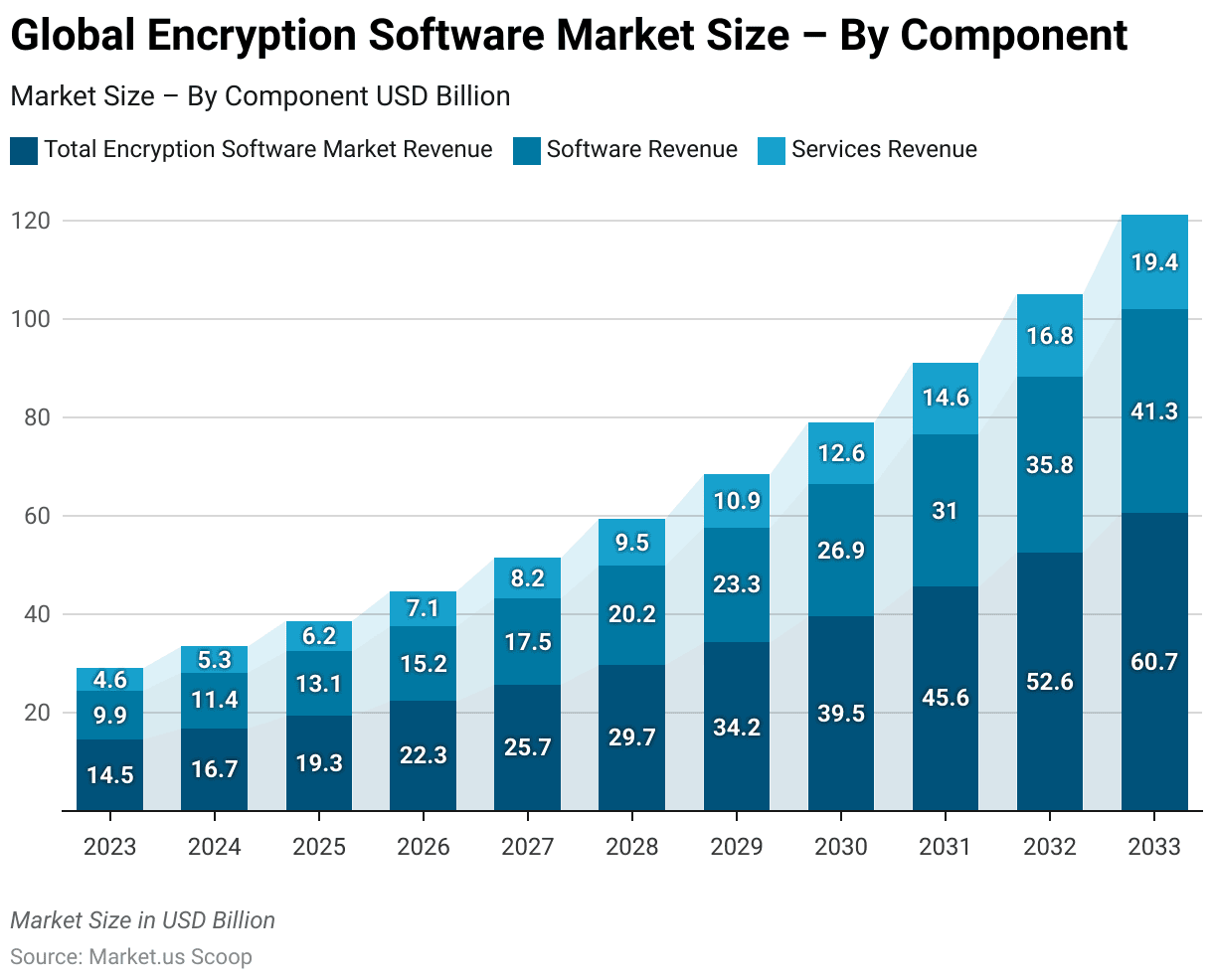
- The global encryption software market is anticipated to exhibit robust growth, with total revenues forecasted to rise from USD 14.5 billion in 2023 to USD 60.7 billion by 2033.
- Within this market, software revenue constitutes a significant portion, expected to grow from USD 9.9 billion in 2023 to USD 41.3 billion by 2033.
- Concurrently, services related to encryption software are also set to see a substantial increase, from USD 4.6 billion in 2023 to USD 19.4 billion in 2033.
- This growth trajectory highlights a rising demand for encryption solutions, with a steady year-on-year expansion in both the software and services sectors.
- The software segment, in particular, demonstrates a larger share of the market revenue, underscoring its critical role in providing robust security measures against cyber threats. At the same time, the services sector growth reflects an increasing need for specialized support and integration services in the encryption domain.
(Source: Market.us)
Use of Enterprise-Wide Encryption Software Solutions Statistics
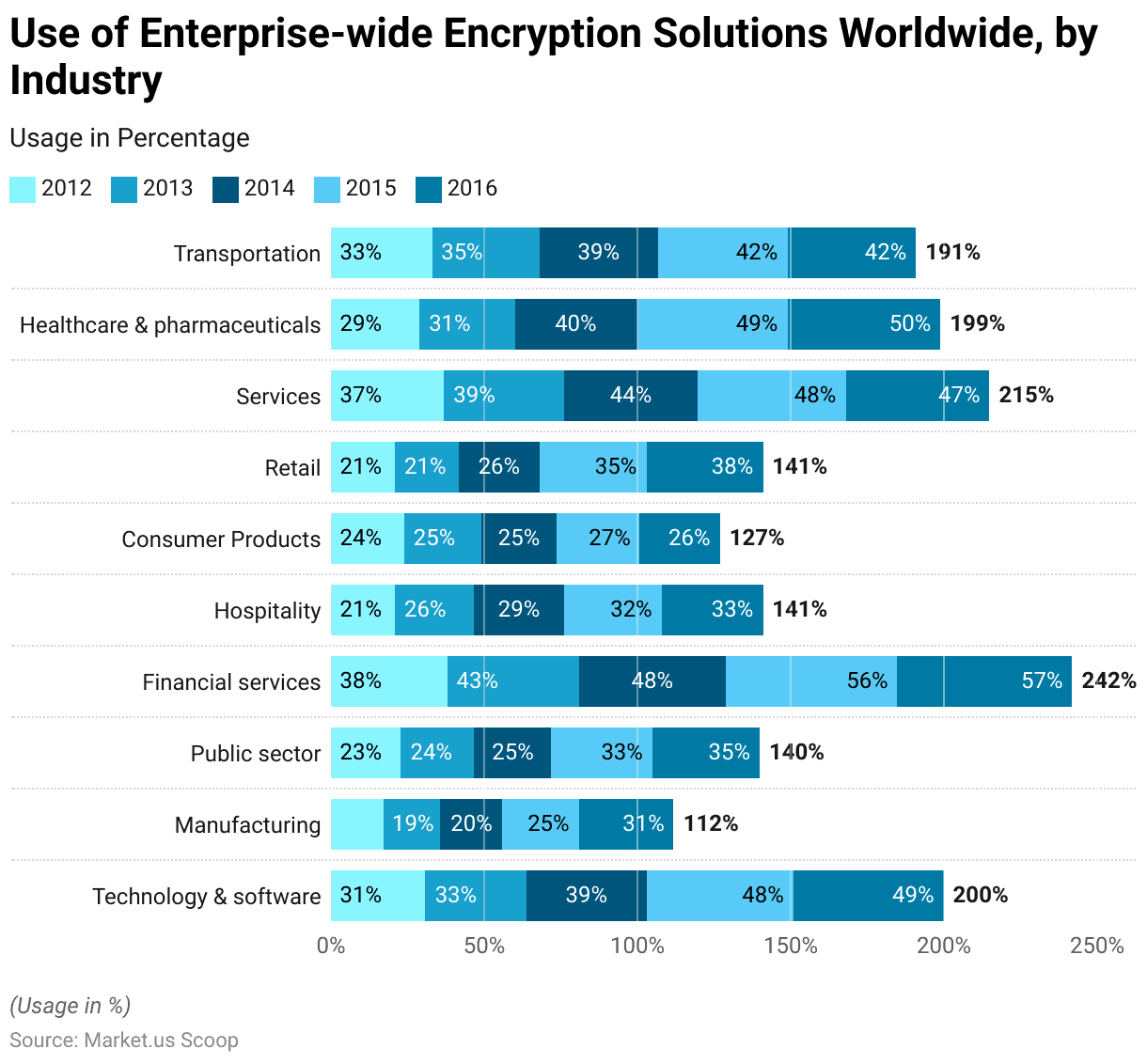
- Over the decade from 2012 to 2022, industries across the board significantly ramped up their adoption of enterprise-wide encryption solutions, as revealed by survey respondents.
- Leading the charge, the technology and software sector saw its adoption figures leap from 31% to a commanding 72%, showcasing its forefront position in encryption uptake.
- Manufacturing followed closely with a jump from 17% to 71%, signaling a growing recognition of the critical importance of data security.
- The public sector also saw substantial growth in encryption use, from 23% to 69%, emphasizing the sector’s focus on safeguarding sensitive data.
- Financial services, which began at a relatively higher starting point of 38% in 2012, increased adoption to 65% by 2022, underlining the sector’s ongoing need for stringent confidentiality measures.
- Other sectors witnessed notable increases as well: hospitality from 21% to 61%, consumer products from 24% to 59%, and retail from 21% to 58%, each demonstrating the broadening scope of encryption’s relevance.
- The services industry, encompassing a diverse array of businesses, grew its encryption implementation from 37% to 57%, stressing its dedication to data security.
- Healthcare and pharmaceuticals, sectors dealing with highly sensitive information, raised their encryption use from 29% to 57%, marking the crucial role of data protection in these areas.
- The transportation sector, integral to logistics and passenger services, increased its encryption adoption from 33% to 54%, reflecting a heightened focus on data-centric security in the face of increasing global movement and connectivity.
(Source: Statista)
Cost of Data Breach for Enterprise Software Statistics
Average Total Cost of a Data Breach
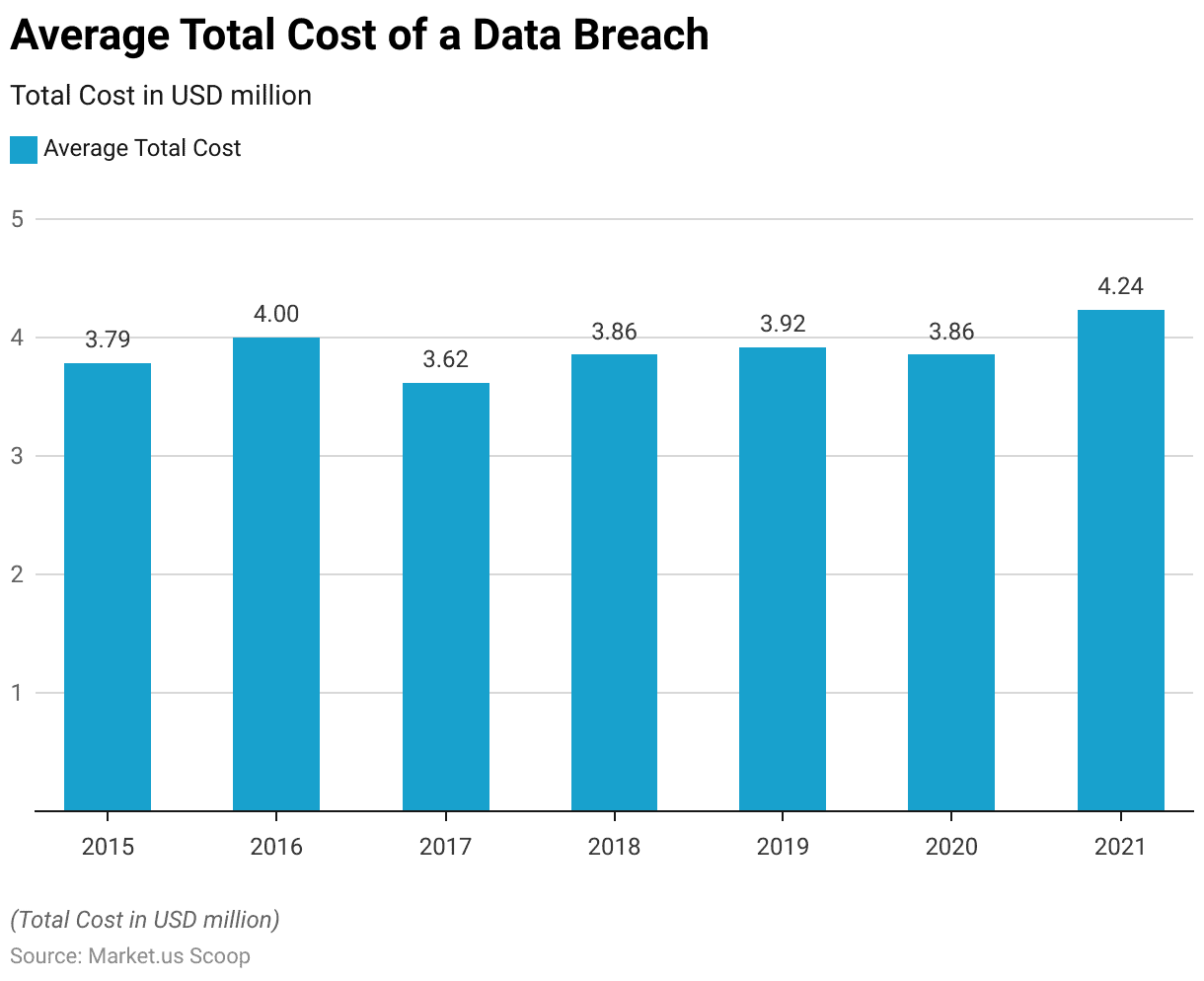
- The average total cost of a data breach, measured in USD million, has exhibited fluctuations over the past seven years.
- In 2015, the average cost stood at 3.79 million USD, experiencing a slight increase to 4.00 million USD in 2016.
- However, the subsequent year witnessed a decrease, with the average cost dropping to 3.62 million USD in 2017.
- This trend of fluctuation persisted as the average total cost rose again to 3.86 million USD in 2018, followed by a minor increase to 3.92 million USD in 2019.
- Despite variations, the average remained relatively consistent in 2020, maintaining a figure of 3.86 million USD.
- However, a notable uptick was observed in 2021, with the average total cost reaching 4.24 million USD, reflecting potential shifts in cybersecurity challenges and mitigation strategies across industries during that period.
(Source: IBM’s Cost of a Data Breach 2021 Report)
Cost of a Data Breach By Average Per Record
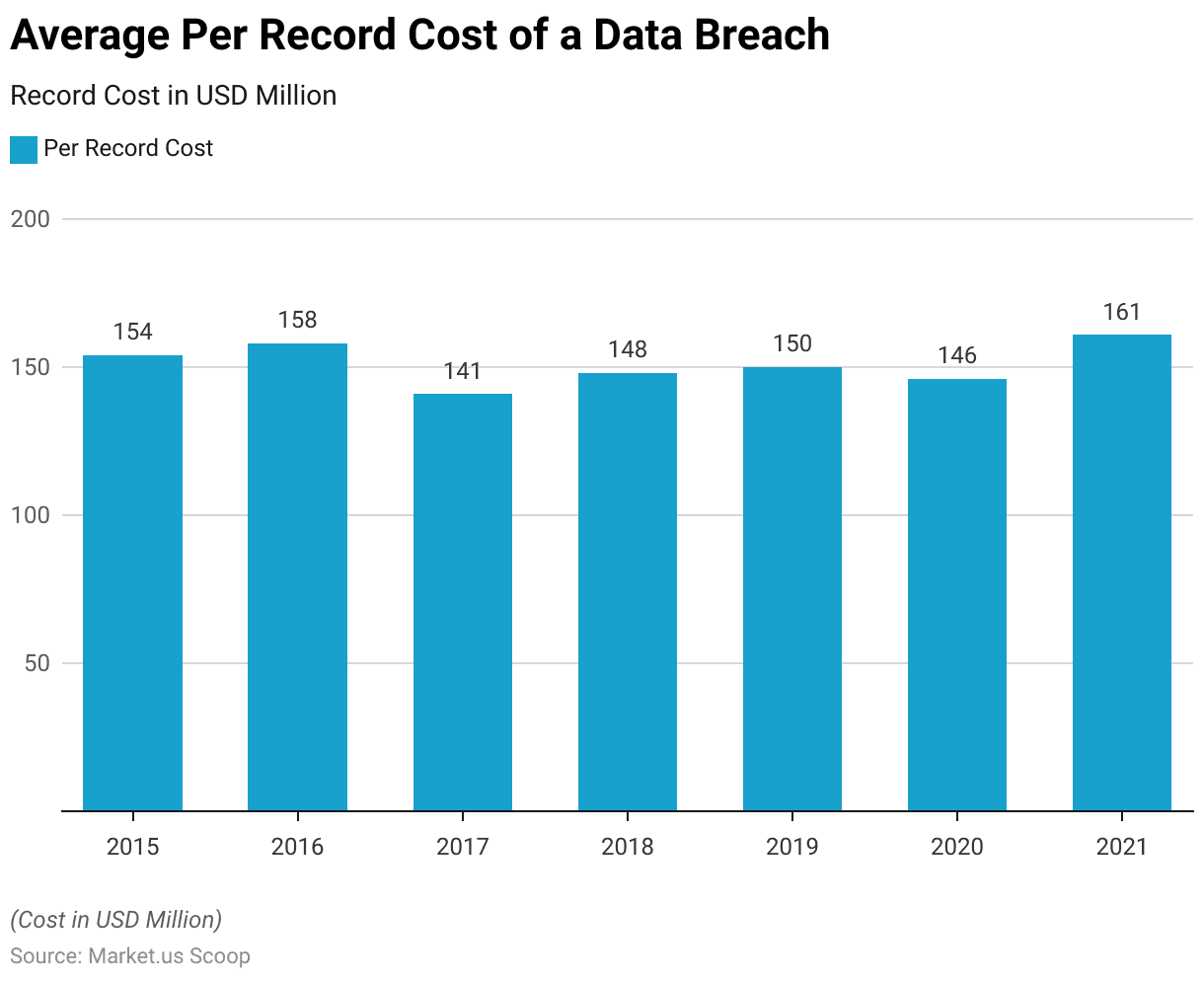
- The average per-record cost of a data breach, denominated in USD, illustrates a nuanced trend over seven years.
- Beginning in 2015 at 154 USD per record, there was a gradual increase to 158 USD in 2016.
- However, a notable decrease occurred in 2017, with the average per-record cost dropping to 141 USD.
- This decline was followed by a modest rise in 2018 to 148 USD and a further slight increase to 150 USD in 2019.
- The subsequent year, 2020, witnessed a marginal decline to 146 USD per record.
- Notably, 2021 saw a significant surge, with the average per-record cost reaching 161 USD, indicating potential shifts in data breach severity and associated costs, potentially influenced by evolving cybersecurity landscapes and regulatory frameworks.
(Source: IBM’s Cost of a Data Breach 2021 Report)
Average Total Cost of a Data Breach by Industry
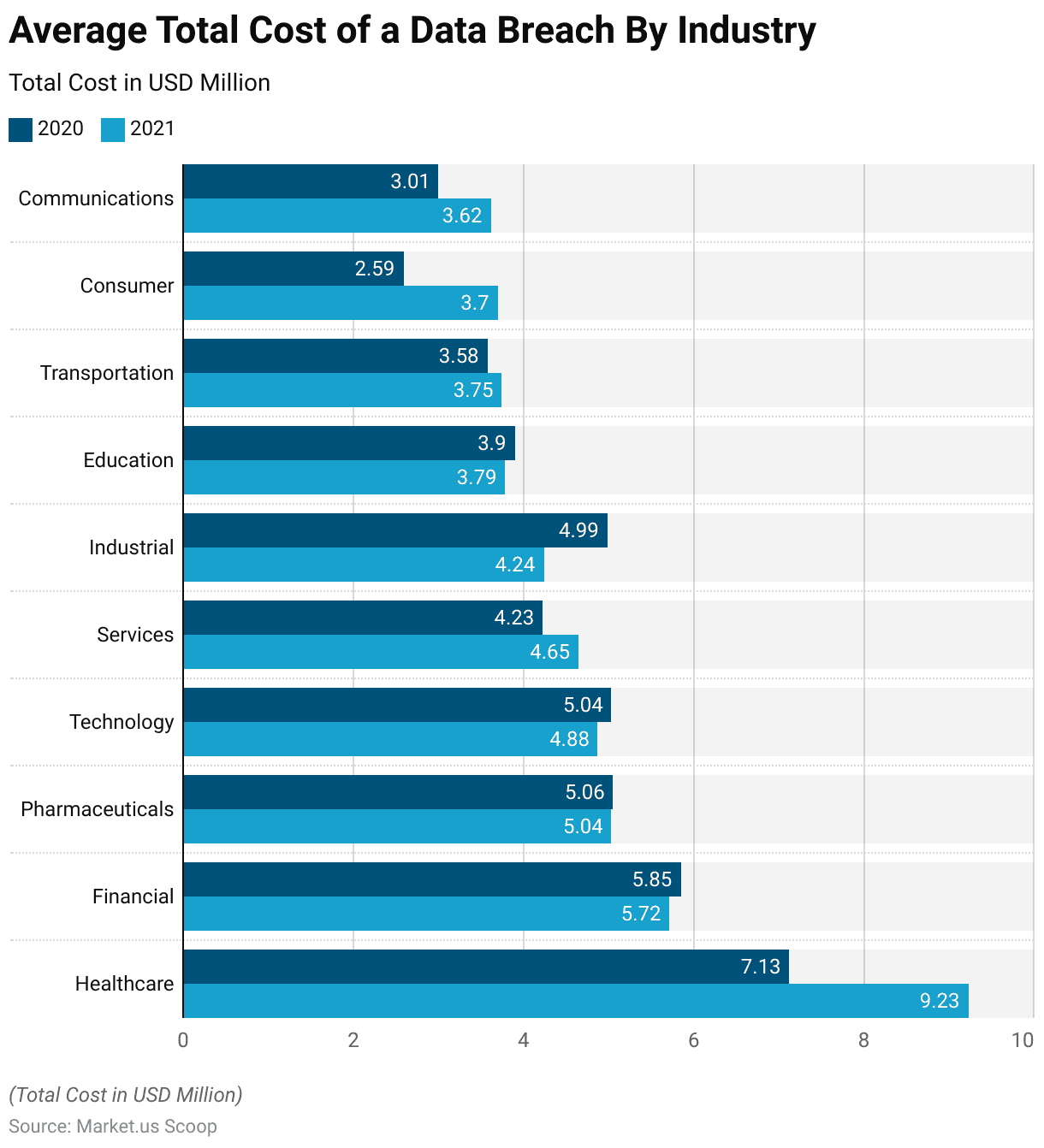
- The average total cost of a data breach varied across industries between the years 2020 and 2021, as depicted in USD million.
- In the healthcare sector, there was a notable increase from 7.13 million USD in 2020 to 9.23 million USD in 2021, reflecting heightened vulnerabilities and potential impacts on patient data security.
- Conversely, the financial industry experienced a slight decrease from 5.85 million USD to 5.72 million USD over the same period, possibly indicative of improved cybersecurity measures or regulatory compliance.
- Similarly, the pharmaceutical and technology sectors also saw marginal decreases, with costs declining from 5.06 million USD to 5.04 million USD and from 5.04 million USD to 4.88 million USD, respectively.
- In contrast, the services industry witnessed a modest rise from 4.23 million USD to 4.65 million USD, while the industrial sector experienced a more pronounced decrease from 4.99 million USD to 4.24 million USD.
- Education and transportation sectors both saw declines, with costs dropping from 3.90 million USD to 3.79 million USD and from 3.58 million USD to 3.75 million USD, respectively.
- Notably, the consumer and communications industries exhibited notable increases in data breach costs, with expenses escalating from 2.59 million USD to 3.70 million USD and from 3.01 million USD to 3.62 million USD, respectively, highlighting potential vulnerabilities and the need for enhanced cybersecurity measures within these sectors.
(Source: IBM’s Cost of a Data Breach 2021 Report)
Identify and Contain a Data Breach By Average Time
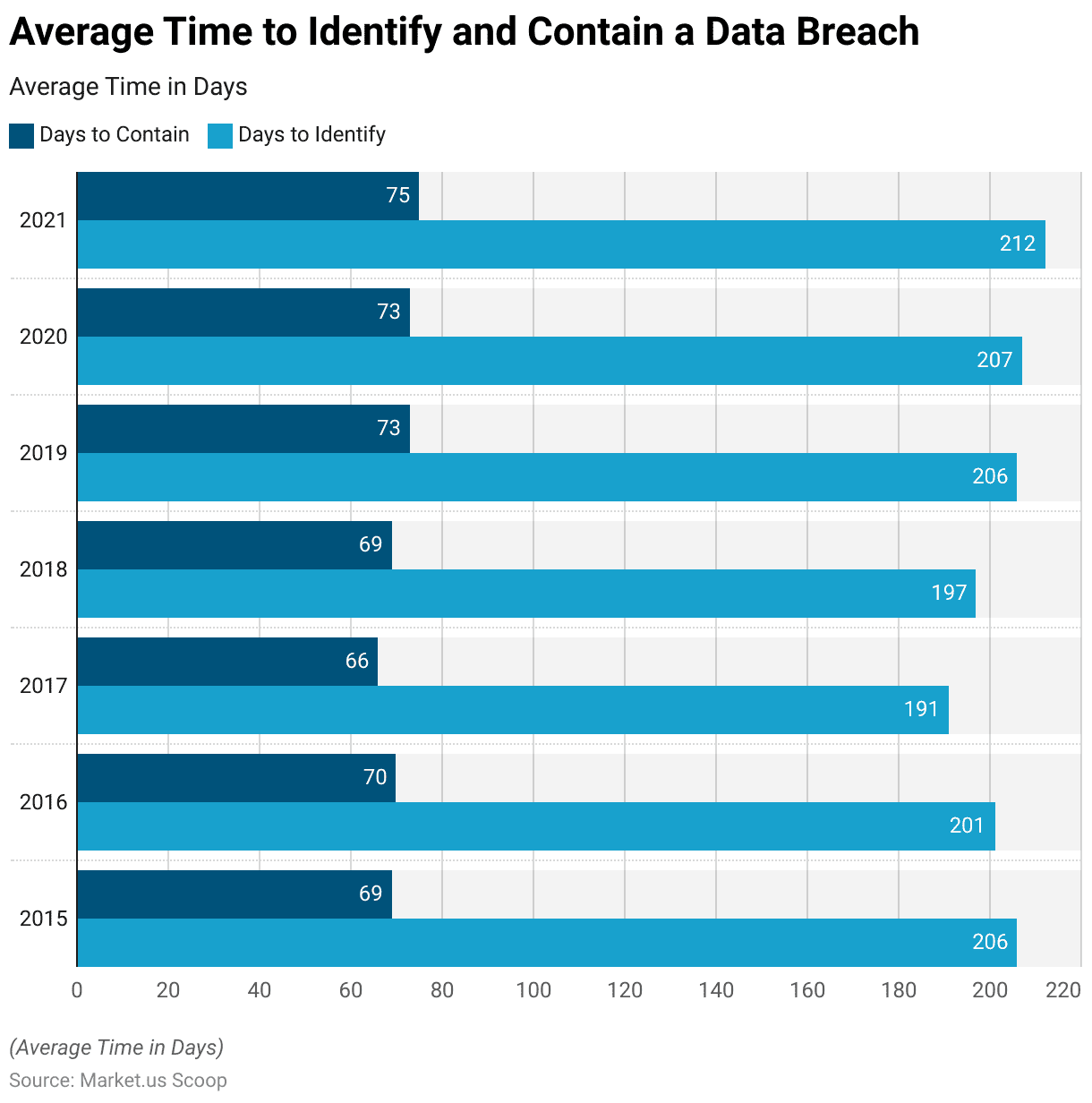
- The average time required to identify and contain a data breach, measured in days, has shown fluctuations over seven years.
- In 2015, it took an average of 206 days to identify a breach and 69 days to contain it.
- The subsequent year, 2016, saw a slight improvement in identification time, decreasing to 201 days, while containment remained relatively stable at 70 days.
- Further progress was noted in 2017, with the average identification time dropping to 191 days and the containment time decreasing to 66 days.
- However, these trends shifted in 2018, as both identification and containment times increased slightly to 197 and 69 days, respectively.
- Despite efforts to expedite responses, the average time to identify and contain breaches rose again in 2019, reaching 206 and 73 days, respectively, and remained relatively consistent in 2020.
- Notably, in 2021, there was a further increase in both identification and containment times, with breaches taking an average of 212 days to identify and 75 days to contain, potentially reflecting the evolving complexities and challenges in data breach detection and mitigation strategies.
(Source: IBM’s Cost of a Data Breach 2021 Report)
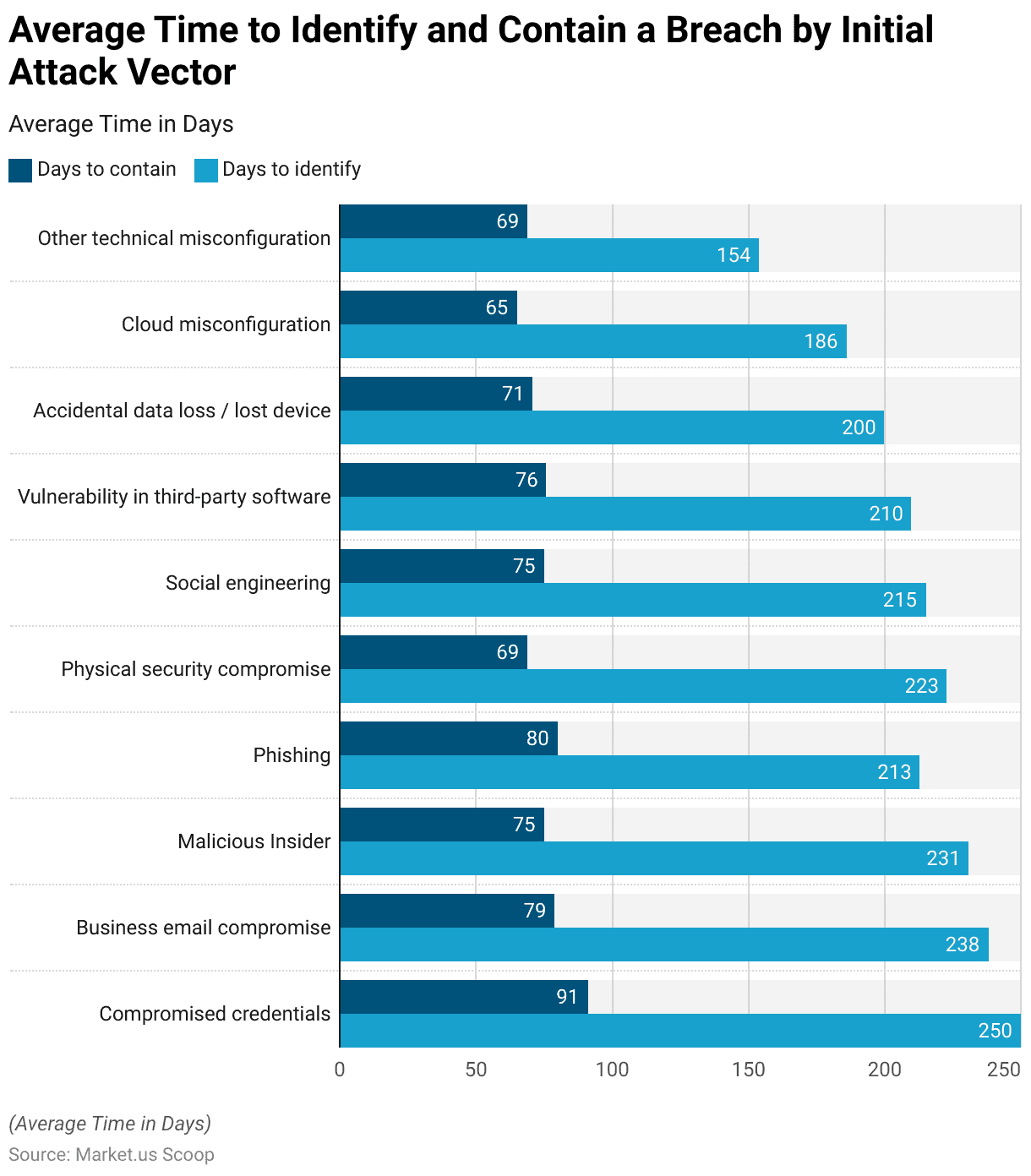
Average Time to Identify and Contain a Breach by Initial Attack Vector
- The average time taken to identify and contain a breach varies significantly depending on the initial attack vector, measured in days.
- Breaches resulting from compromised credentials had the longest identification period, averaging 250 days, and were also among the lengthiest to contain, with an average of 91 days.
- Similarly, business email compromise incidents required considerable time to detect and resolve, with an average identification period of 238 days and a containment period of 79 days.
- Malicious insider activities and phishing attacks also demanded significant resources and time, with average identification periods of 231 and 213 days and containment periods of 75 and 80 days, respectively.
- Physical security compromises and social engineering attacks had relatively shorter identification and containment periods compared to other vectors, averaging 223 and 215 days for identification and 69 and 75 days for containment, respectively.
- Vulnerabilities in third-party software and accidental data loss incidents had somewhat shorter identification and containment periods, with averages of 210 and 200 days for identification and 76 and 71 days for containment, respectively.
- Notably, breaches due to cloud misconfigurations had a shorter containment period of 65 days despite a longer identification period of 186 days.
- Similarly, other technical misconfigurations had a longer identification period of 154 days but a shorter containment period of 69 days.
- These findings underscore the critical importance of promptly identifying and containing breaches, especially those stemming from compromised credentials and business email compromise, to mitigate risks effectively and minimize potential damages.
(Source: IBM’s Cost of a Data Breach 2021 Report)
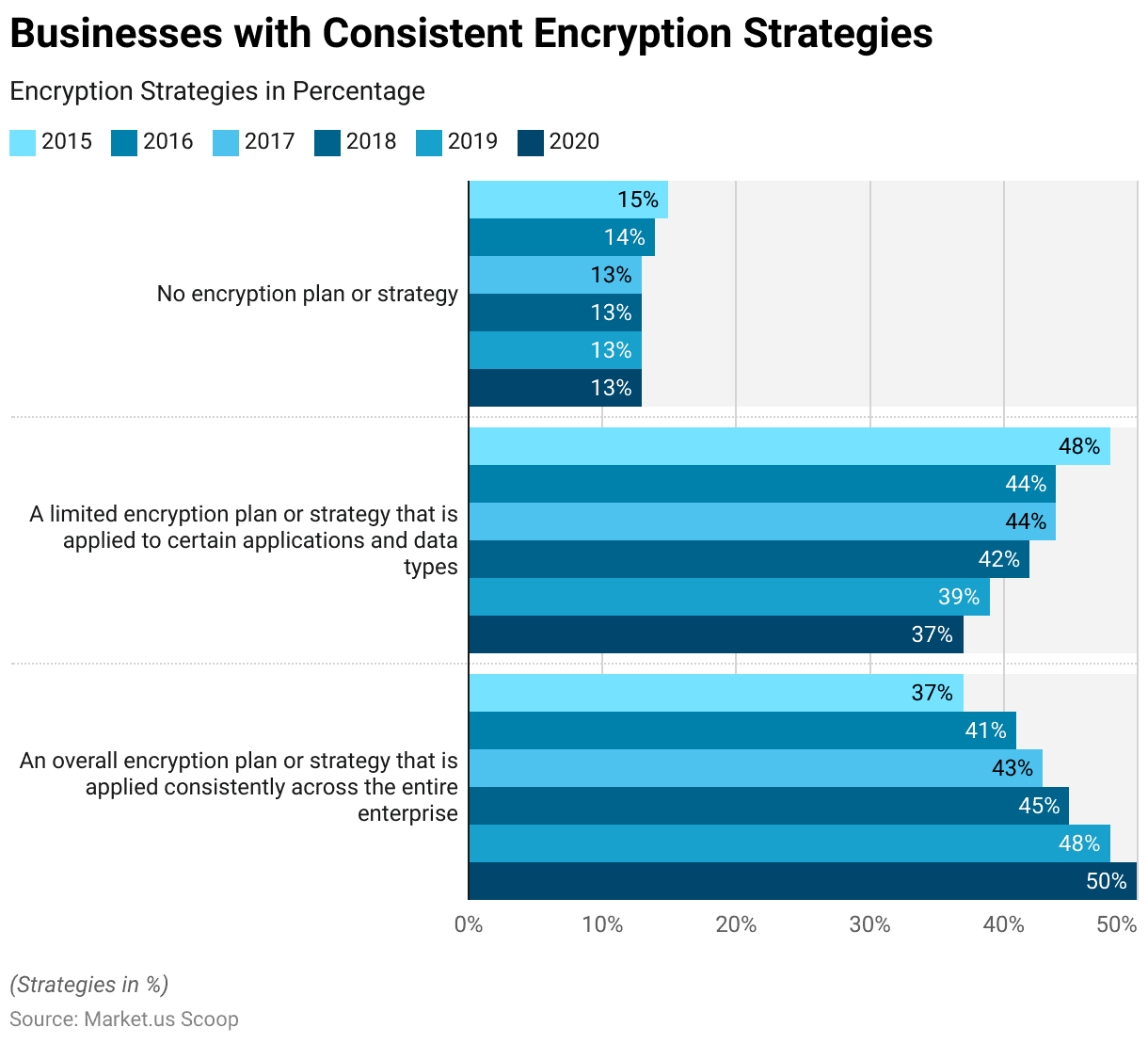
Businesses with Consistent Software Encryption Statistics
- Over six years, there has been a noticeable trend in the adoption of encryption strategies among businesses.
- In 2015, 37% of businesses reported implementing an overall encryption plan or strategy consistently across their entire enterprise. Meanwhile, 48% had a limited encryption plan applied to specific applications and data types, leaving 15% with no encryption strategy in place.
- Subsequently, there was a gradual increase in the adoption of consistent encryption strategies, with the percentage rising to 50% in 2020.
- Conversely, the proportion of businesses with limited encryption plans decreased steadily from 44% in 2016 to 37% in 2020.
- Notably, the percentage of businesses without any encryption plan remained relatively stable throughout the period, hovering around 13%.
- These findings reflect a growing recognition of the importance of encryption in safeguarding sensitive data, as evidenced by the increasing adoption of consistent encryption strategies across enterprises over the years.
(Source: Ponemon 2021 Encryption Trends Strategy)
Recent Developments:
Acquisitions and Mergers:
- In the past year, the encryption software industry has witnessed 10 acquisitions and mergers, indicating consolidation and strategic alliances among key players.
Funding and Investment:
- Encryption software startups secured $50 million in funding from venture capital firms and investors, fueling research, development, and market expansion efforts.
Strategic Partnerships:
- The industry saw 8 strategic partnerships formed between encryption software providers and technology companies, enhancing product offerings and market reach.
Regulatory Compliance:
- With increasing data privacy regulations, encryption software adoption surged, with 20% of companies investing in compliance solutions.
Cybersecurity Threats:
- The rise in cyber threats led to 25% more reported incidents, driving demand for encryption software to protect sensitive data.
Conclusion
Encryption Software Statistics – The surge in encryption software use from 2012 to 2022 highlights a global move towards enhancing data security and privacy across industries.
This growth indicates an increasing awareness of encryption’s critical role in defending against cyber threats and securing sensitive data.
Led by the technology and software sector, with significant adoption in manufacturing, financial services, and healthcare, organizations are keenly adopting encryption to meet regulatory demands, protect customer information, and build trust in a digitally transforming world.
As cyber threats evolve, encryption remains a key component of cybersecurity strategies. Future innovations and broader applications of encryption technologies are expected to secure our digital landscape further.
This period marks the beginning of an era that promises even wider adoption and advancements in encryption, pointing towards a safer digital future.
FAQs
Encryption software is a tool designed to secure digital data by converting it into a coded format, known as ciphertext, which cannot be easily interpreted without the correct decryption key. This process helps protect the data from unauthorized access, theft, or exposure.
Encryption software uses cryptographic algorithms to transform readable data (plaintext) into an unreadable format (ciphertext). To access the original data, the correct decryption key is required. There are two main types of encryption: symmetric (using the same key for encryption and decryption) and asymmetric (using a pair of keys, public for encryption and private for decryption).
In today’s digital age, data breaches and cyber threats are increasingly common. Encryption software plays a crucial role in protecting sensitive information such as personal data, financial records, and confidential communications from unauthorized access and cyber-attacks.
Any individual or organization that handles sensitive data should consider using encryption software. This includes businesses of all sizes, government agencies, healthcare providers, financial institutions, and private users who wish to protect their personal information.
When selecting encryption software, consider its encryption strength (algorithm and key length), ease of use, compatibility with your systems, performance impact, and compliance with relevant regulations and standards.


