Table of Contents
- Introduction
- Editor’s Choice
- Global Encryption Software Market Overview
- Use of Enterprise-Wide Encryption Solutions Worldwide – By Industry
- Cost of Data Breach Driving the Demand for Enterprise Software
- Data Breach Average Time to Identify and Contains
- Average Time to Identify and Contain a Breach by Initial Attack Vector
- Businesses with Consistent Encryption Strategies
Introduction
According to Encryption Software Statistics, Encryption software is essential for protecting digital data, using cryptographic algorithms to turn readable information into a secured format to prevent unauthorized access.
It includes symmetric encryption, which uses one key for both encrypting and decrypting, ideal for handling vast amounts of data quickly, and asymmetric encryption, which uses a key pair for securing data exchanges and verifying user identities.
Its uses are widespread, from securing data and communications to ensuring the authenticity and integrity of information.
When choosing encryption software, factors like encryption strength, system performance impact, ease of use, and regulatory compliance are crucial.
Addressing challenges like secure key management and regulatory adherence is vital for maintaining effective data protection, highlighting the need for ongoing strategy adjustments to face new threats and technological changes.
Editor’s Choice
- The global encryption software market revenue is expected to reach USD 60.7 billion by 2033.
- Within this market, software revenue constitutes a significant portion, expected to grow from USD 9.9 billion in 2023 to USD 41.3 billion by 2033.
- Over the decade from 2012 to 2022, among various industries, the technology and software sector saw its adoption figures leap from 31% to a commanding 72%, showcasing its forefront position in encryption uptake.
- A notable uptick was observed in 2021, with the average total cost reaching 4.24 million USD, reflecting potential shifts in cybersecurity challenges and mitigation strategies across industries.
- 2021 saw a significant surge, with the average per-record cost reaching 161 USD, indicating potential shifts in data breach severity and associated costs, potentially influenced by evolving cybersecurity landscapes and regulatory frameworks.
- Notably, in 2021, there was a further increase in both identification and containment times, with breaches taking an average of 212 days to identify and 75 days to contain, potentially reflecting the evolving complexities and challenges in data breach detection and mitigation strategies.
- In 2015, 37% of businesses reported implementing an overall encryption plan or strategy consistently across their entire enterprise.

Global Encryption Software Market Overview
Encryption Software Market Size
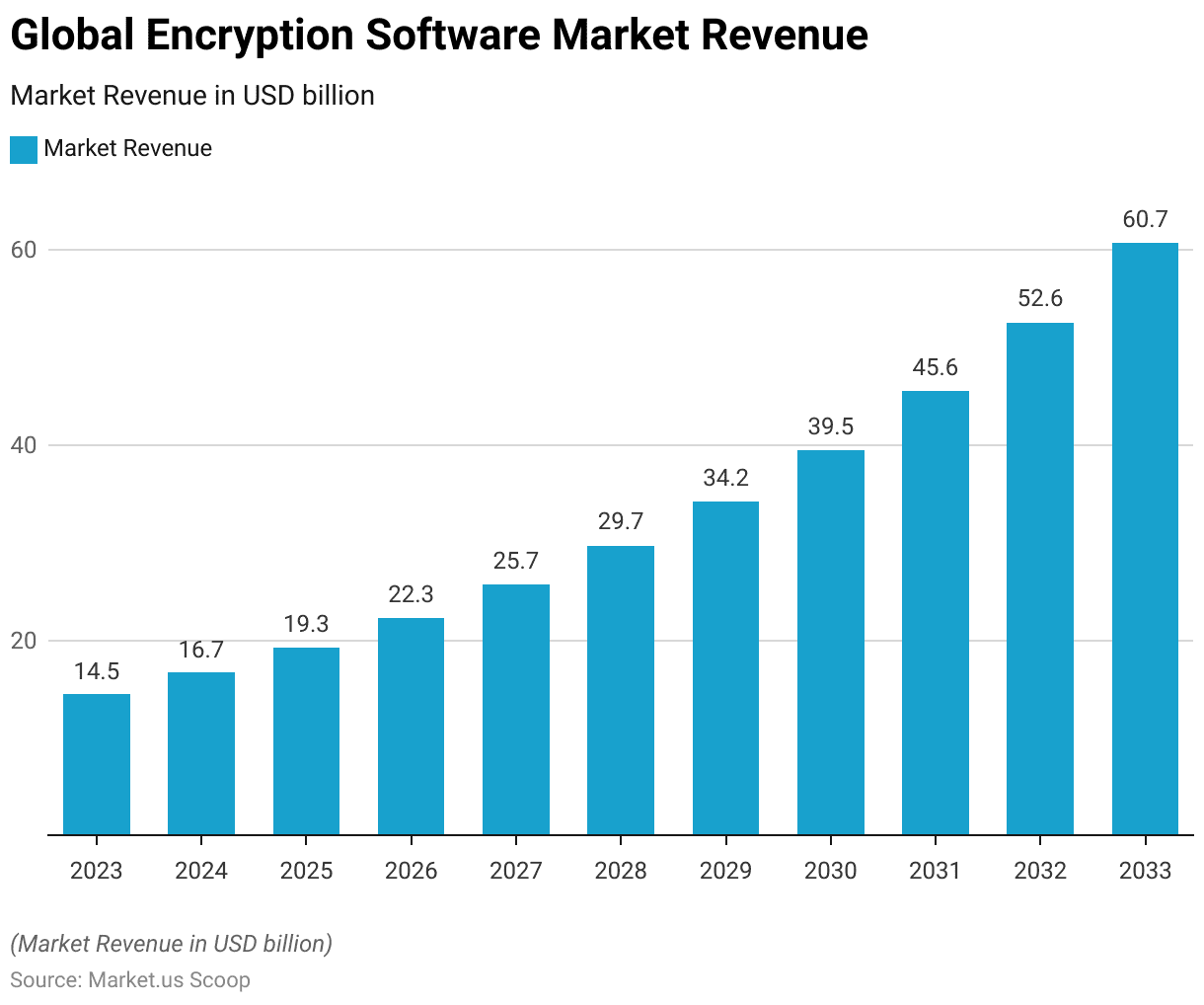
- The global encryption software market is projected to experience substantial growth over the next decade at a CAGR of 15.4%, with revenues forecasted to increase from USD 14.5 billion in 2023 to USD 60.7 billion by 2033.
- This upward trend highlights a compound annual growth rate, starting with USD 16.7 billion in 2024 and showing steady increases: USD 19.3 billion in 2025, USD 22.3 billion in 2026, and USD 25.7 billion by 2027.
- The market is expected to continue its expansion, reaching USD 29.7 billion in 2028, USD 34.2 billion in 2029, and USD 39.5 billion in 2030, before accelerating to USD 45.6 billion in 2031, USD 52.6 billion in 2032, and finally, USD 60.7 billion in 2033.
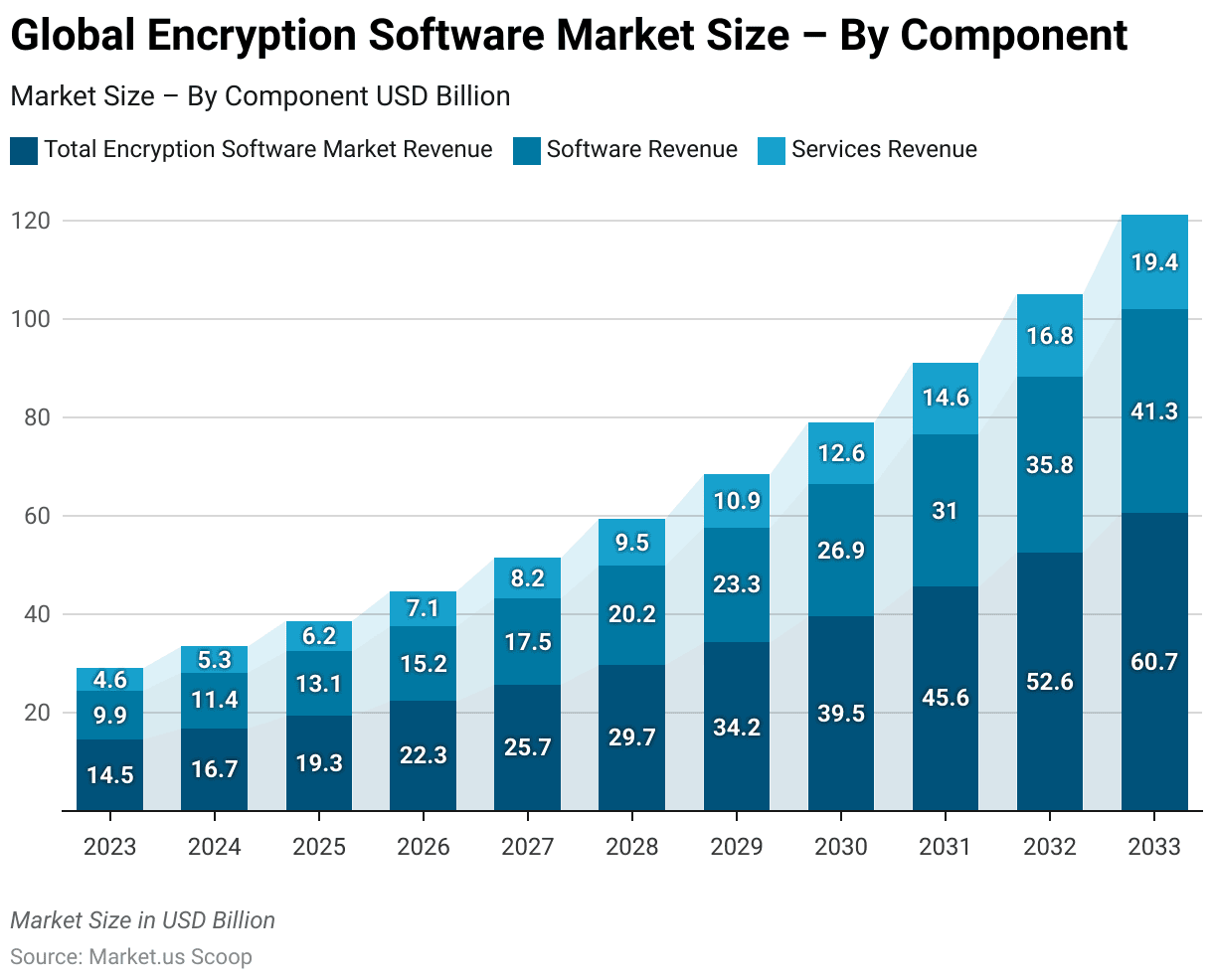
Global Encryption Software Market Size – By Component
- The global encryption software market is anticipated to exhibit robust growth, with total revenues forecasted to rise from USD 14.5 billion in 2023 to USD 60.7 billion by 2033.
- Within this market, software revenue constitutes a significant portion, expected to grow from USD 9.9 billion in 2023 to USD 41.3 billion by 2033.
- Concurrently, services related to encryption software are also set to see a substantial increase, from USD 4.6 billion in 2023 to USD 19.4 billion in 2033.
- This growth trajectory highlights a rising demand for encryption solutions, with a steady year-on-year expansion in both the software and services sectors.
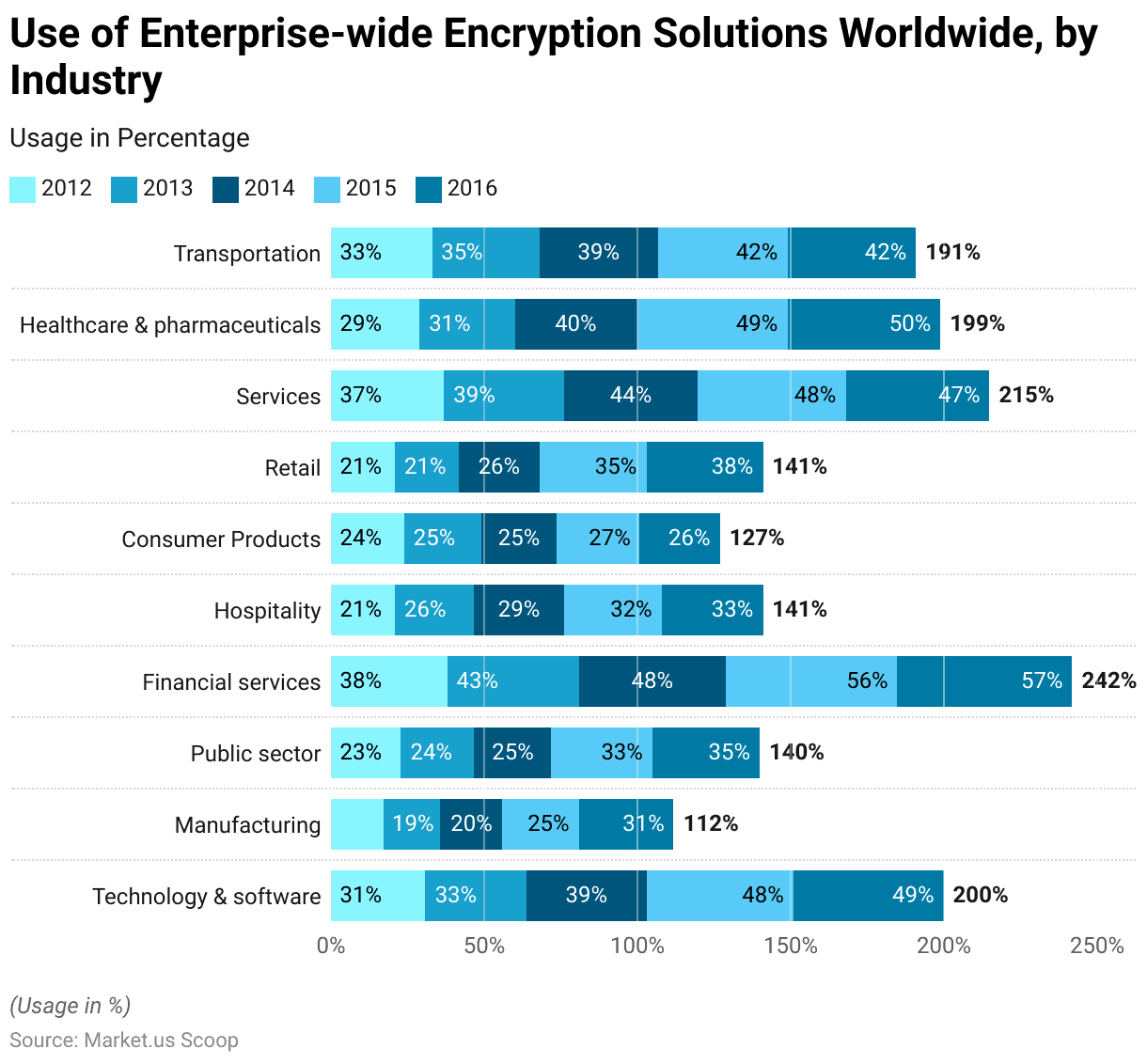
Use of Enterprise-Wide Encryption Solutions Worldwide – By Industry
- Over the decade from 2012 to 2022, industries across the board significantly ramped up their adoption of enterprise-wide encryption solutions, as revealed by survey respondents.
- Leading the charge, the technology and software sector saw its adoption figures leap from 31% to a commanding 72%, showcasing its forefront position in encryption uptake.
- Manufacturing followed closely with a jump from 17% to 71%, signaling a growing recognition of the critical importance of data-centric security.
- The public sector also saw substantial growth in encryption use, from 23% to 69%, emphasizing the sector’s focus on safeguarding sensitive data.
- Financial services, which began at a relatively higher starting point of 38% in 2012, increased adoption to 65% by 2022, underlining the sector’s ongoing need for stringent confidentiality measures.
- Other sectors witnessed notable increases as well: hospitality from 21% to 61%, consumer products from 24% to 59%, and retail from 21% to 58%, each demonstrating the broadening scope of encryption’s relevance.
Cost of Data Breach Driving the Demand for Enterprise Software
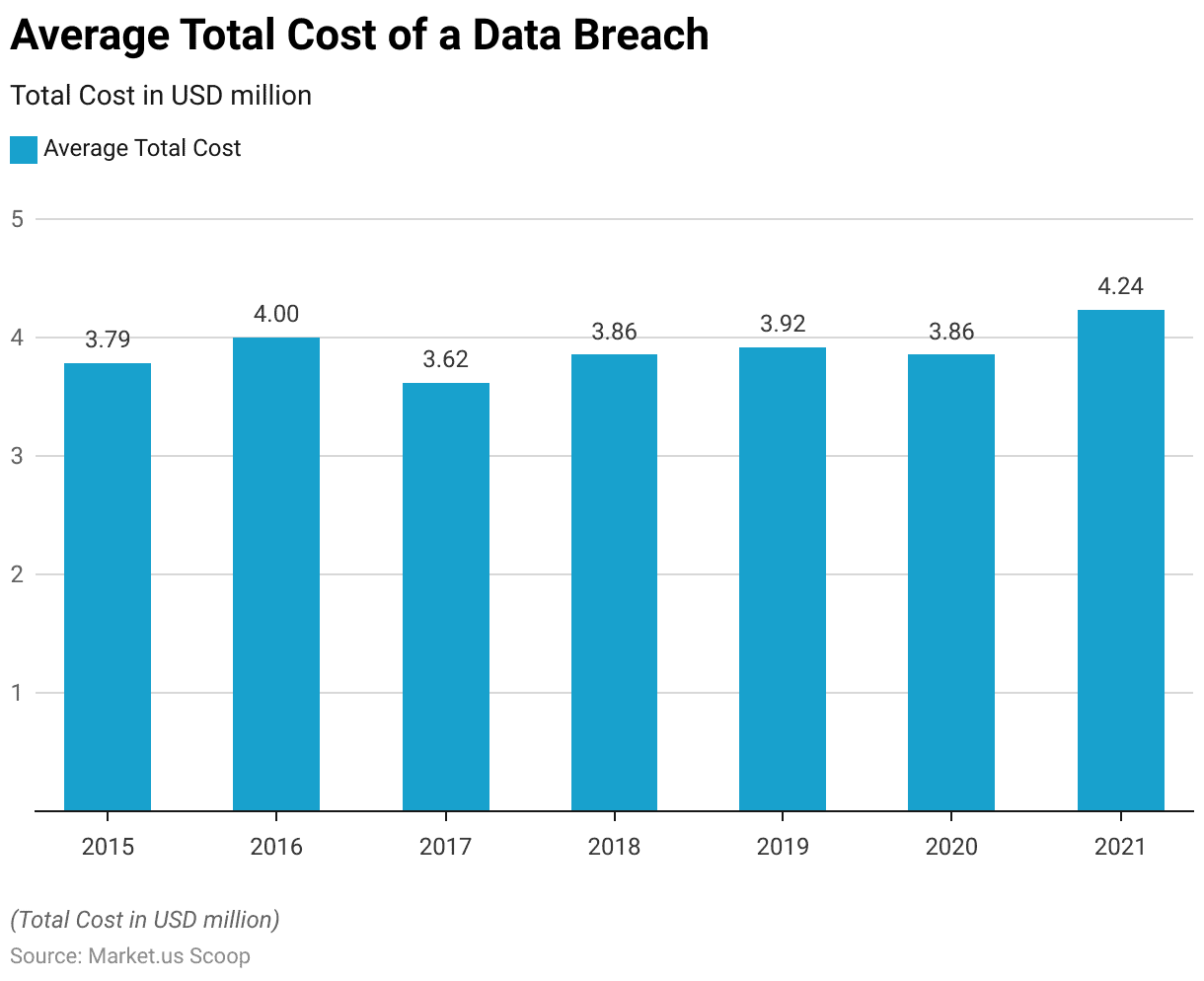
Average Total Cost of a Data Breach
- The average total cost of a data breach, measured in USD million, has exhibited fluctuations over the past seven years.
- In 2015, the average cost stood at 3.79 million USD, experiencing a slight increase to 4.00 million USD in 2016.
- Despite variations, the average remained relatively consistent in 2020, maintaining a figure of 3.86 million USD.
- However, a notable uptick was observed in 2021, with the average total cost reaching 4.24 million USD, reflecting potential shifts in cybersecurity challenges and mitigation strategies across industries during that period.
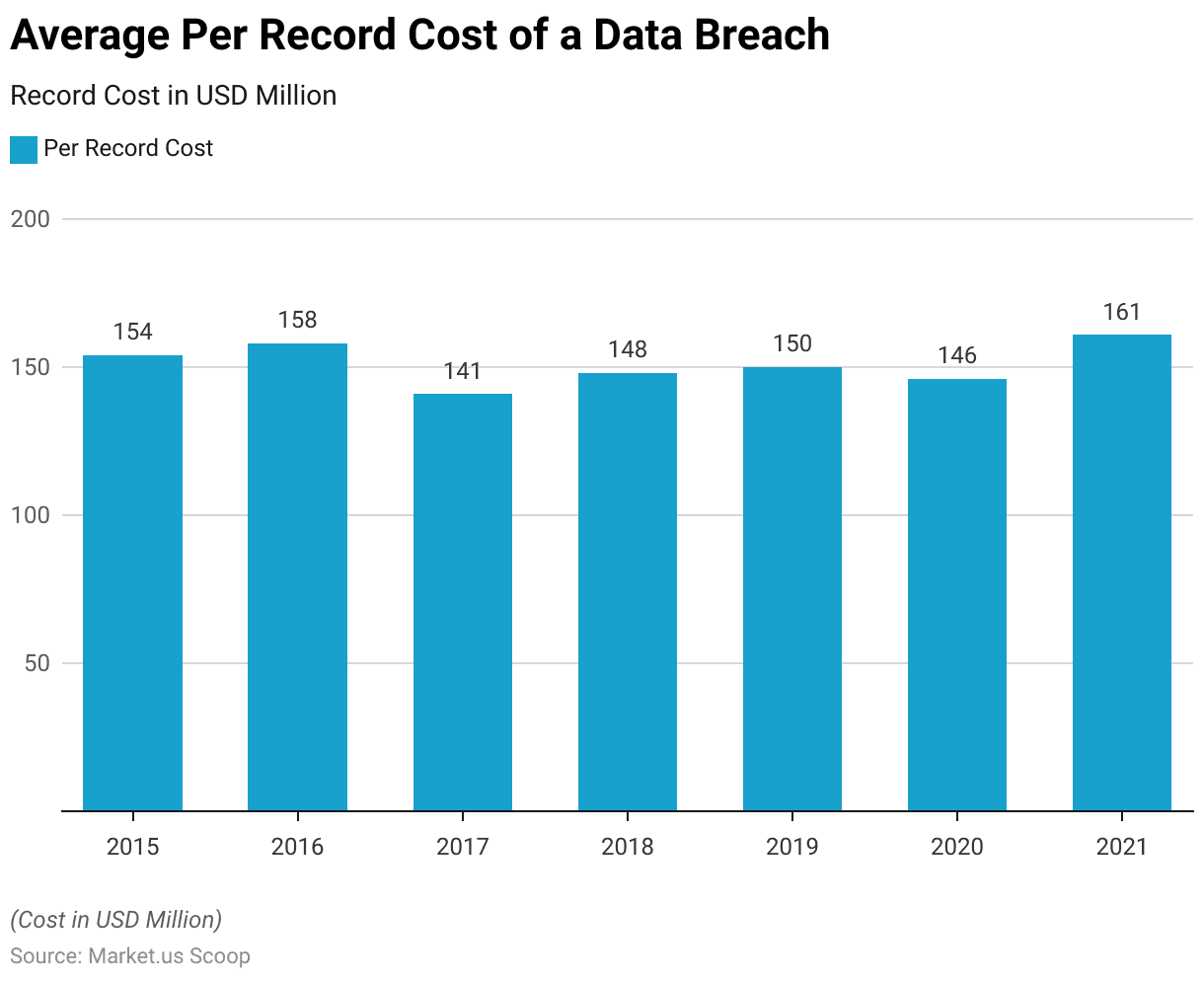
Cost of a Data Breach Average Per Record
- The average per-record cost of a data breach, denominated in USD, illustrates a nuanced trend over seven years.
- Beginning in 2015 at 154 USD per record, there was a gradual increase to 158 USD in 2016.
- However, a notable decrease occurred in 2017, with the average per-record cost dropping to 141 USD.
- This decline was followed by a modest rise in 2018 to 148 USD and a further slight increase to 150 USD in 2019.
- The subsequent year, 2020, witnessed a marginal decline to 146 USD per record.
- Notably, 2021 saw a significant surge, with the average per-record cost reaching 161 USD, indicating potential shifts in data breach severity and associated costs.
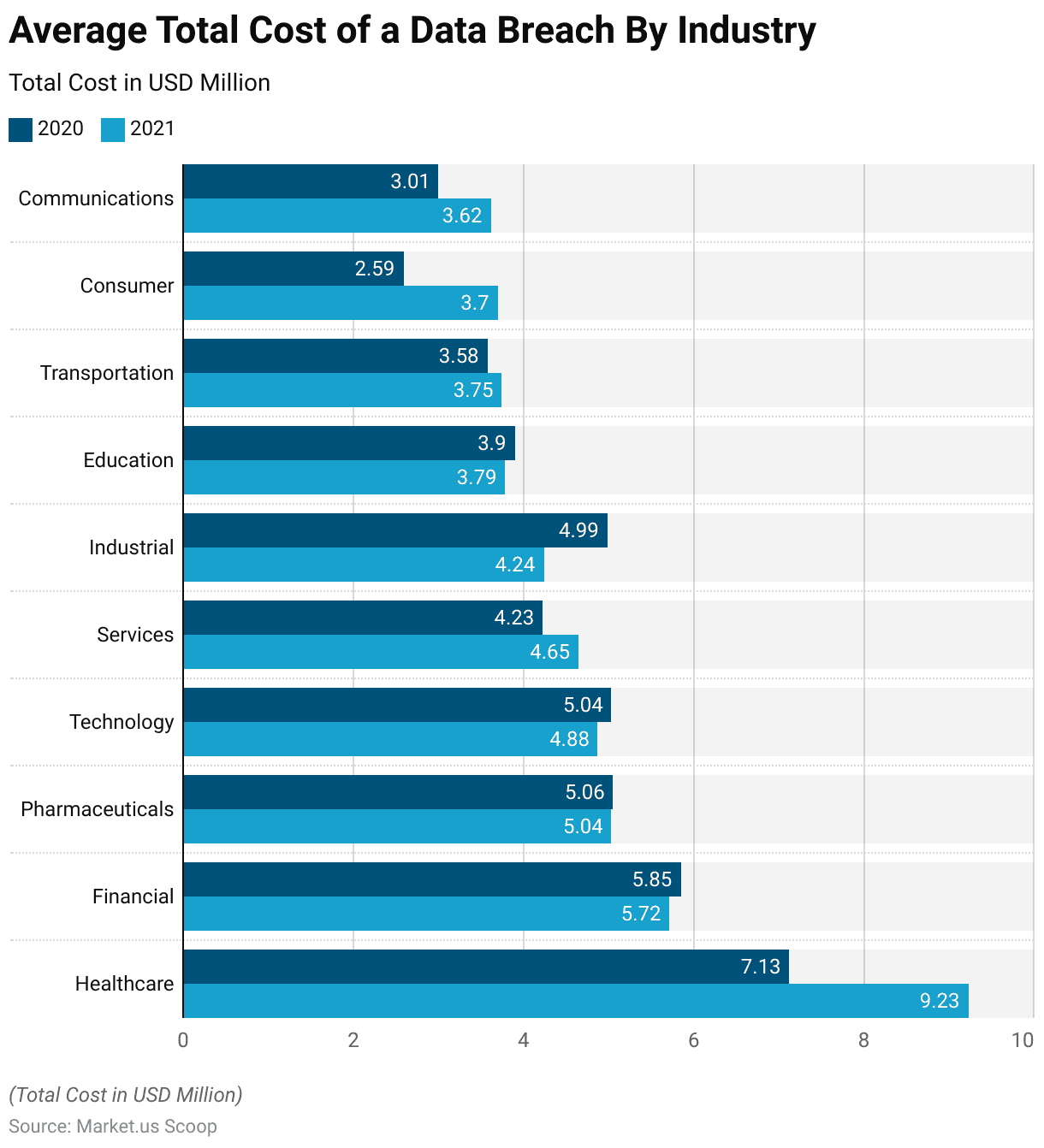
Average Total Cost of a Data Breach by Industry
- The average total cost of a data breach varied across industries between the years 2020 and 2021, as depicted in USD million.
- In the healthcare sector, there was a notable increase from 7.13 million USD in 2020 to 9.23 million USD in 2021, reflecting heightened vulnerabilities and potential impacts on patient data security.
- Conversely, the financial industry experienced a slight decrease from 5.85 million USD to 5.72 million USD over the same period, possibly indicative of improved cybersecurity measures or regulatory compliance.
- Similarly, the pharmaceutical and technology sectors also saw marginal decreases, with costs declining from 5.06 million USD to 5.04 million USD and from 5.04 million USD to 4.88 million USD, respectively.
- In contrast, the services industry witnessed a modest rise from 4.23 million USD to 4.65 million USD, while the industrial sector experienced a more pronounced decrease from 4.99 million USD to 4.24 million USD.
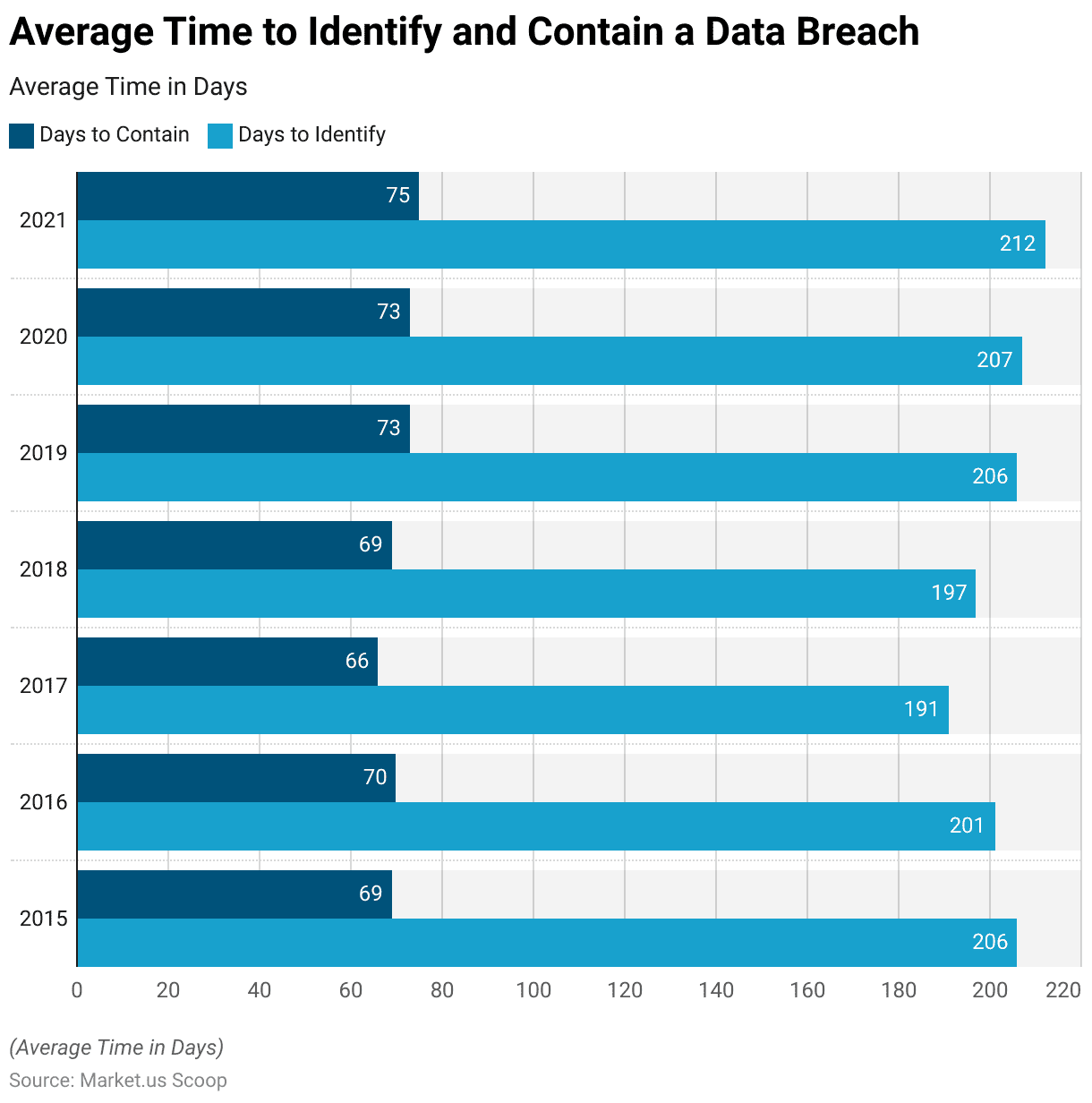
Data Breach Average Time to Identify and Contains
- The average time required to identify and contain a data breach, measured in days, has shown fluctuations over seven years.
- In 2015, it took an average of 206 days to identify a breach and 69 days to contain it.
- The subsequent year, 2016, saw a slight improvement in identification time, decreasing to 201 days, while containment remained relatively stable at 70 days.
- Despite efforts to expedite responses, the average time to identify and contain breaches rose again in 2019, reaching 206 and 73 days, respectively, and remained relatively consistent in 2020.
- Notably, in 2021, there was a further increase in both identification and containment times, with breaches taking an average of 212 days to identify and 75 days to contain, potentially reflecting the evolving complexities and challenges in data breach detection and mitigation strategies.
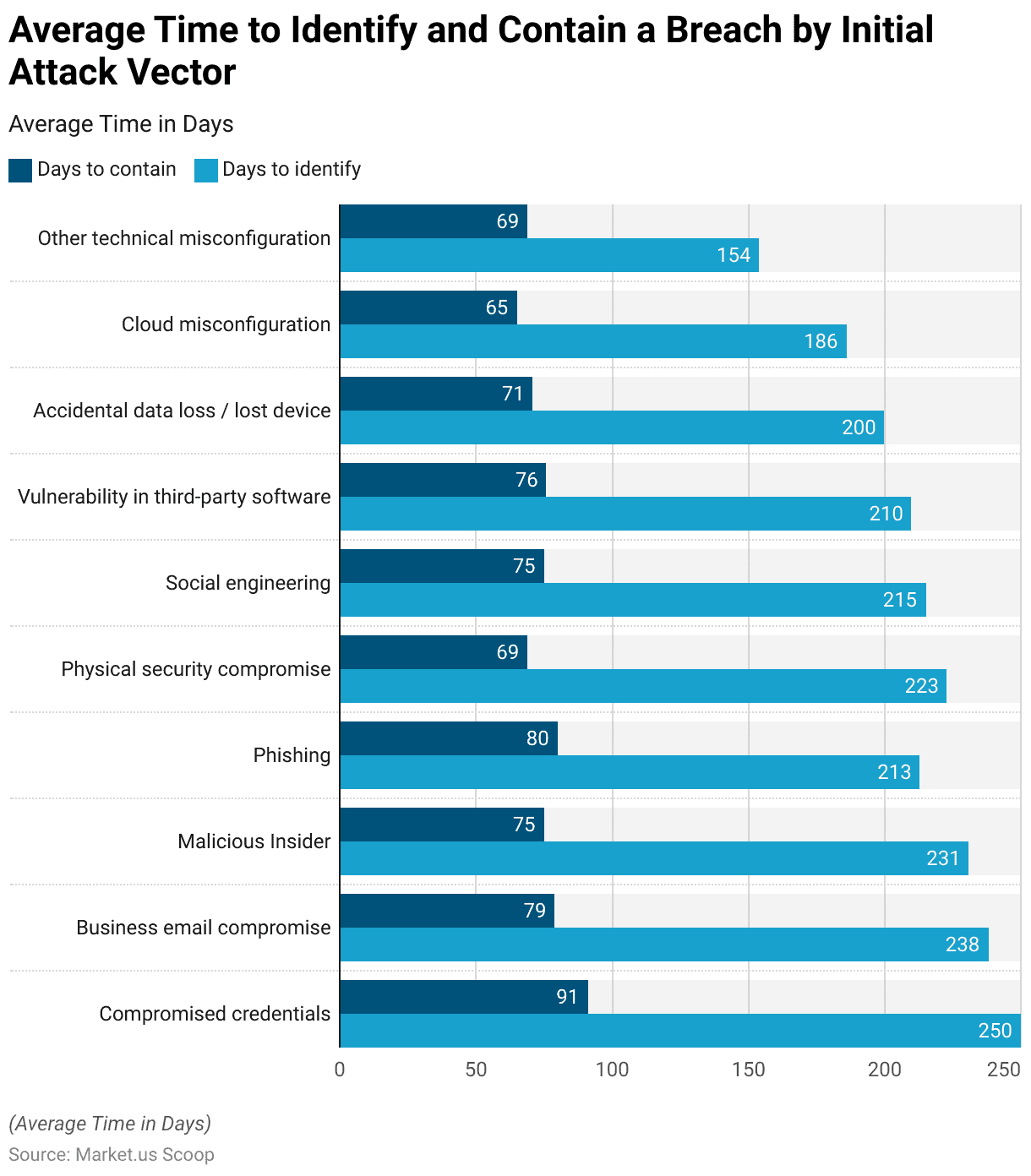
Average Time to Identify and Contain a Breach by Initial Attack Vector
- The average time taken to identify and contain a breach varies significantly depending on the initial attack vector, measured in days.
- Breaches resulting from compromised credentials had the longest identification period, averaging 250 days, and were also among the lengthiest to contain, with an average of 91 days.
- Similarly, business email compromise incidents required considerable time to detect and resolve, with an average identification period of 238 days and a containment period of 79 days.
- Malicious insider activities and phishing attacks also demanded significant resources and time, with average identification periods of 231 and 213 days and containment periods of 75 and 80 days, respectively.
- Physical security compromises and social engineering attacks had relatively shorter identification and containment periods compared to other vectors, averaging 223 and 215 days for identification and 69 and 75 days for containment, respectively.
- Vulnerabilities in third-party software and accidental data loss incidents had somewhat shorter identification and containment periods, with averages of 210 and 200 days for identification and 76 and 71 days for containment, respectively.
- Notably, breaches due to cloud misconfigurations had a shorter containment period of 65 days despite a longer identification period of 186 days.
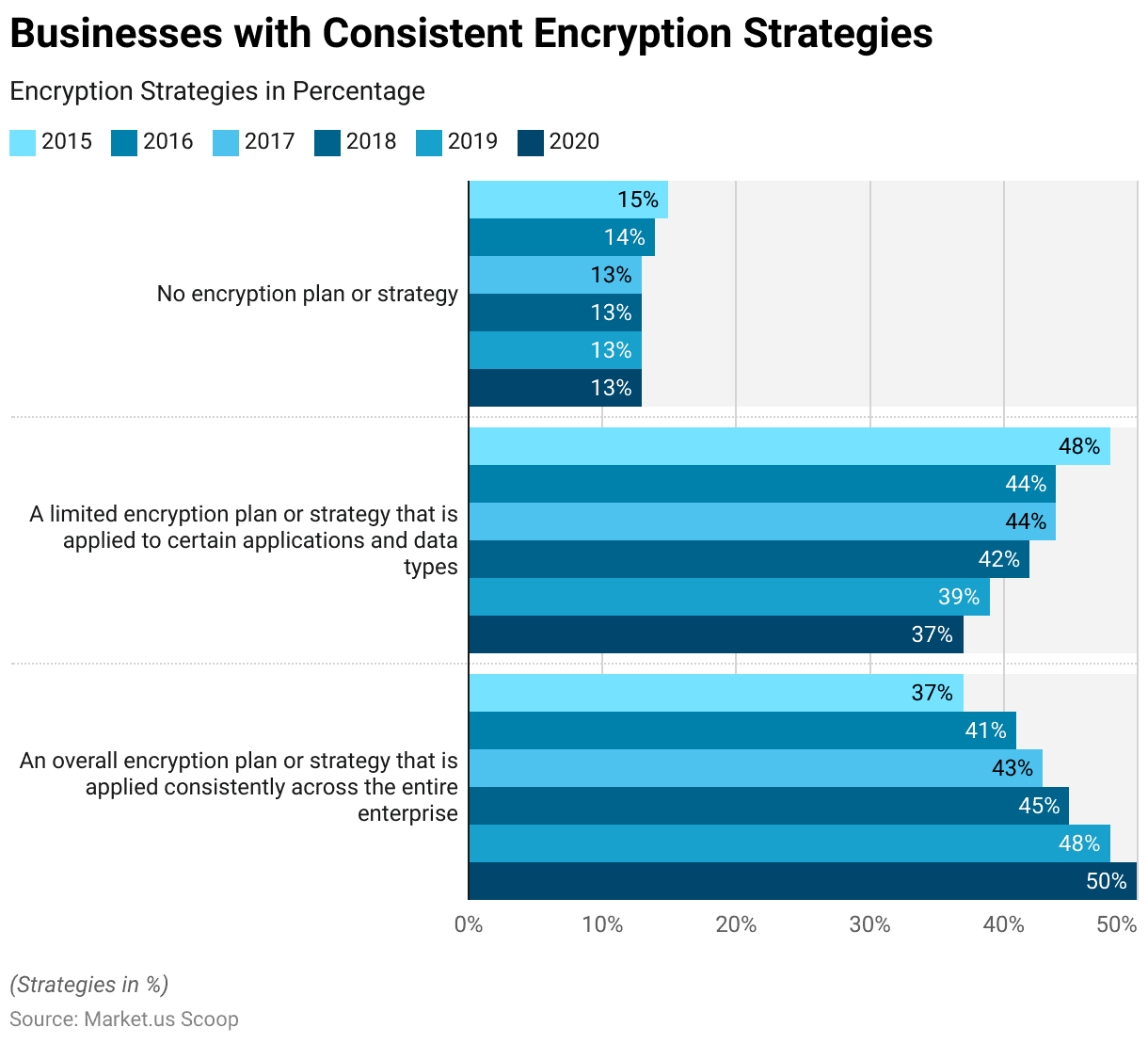
Businesses with Consistent Encryption Strategies
- Over 6 years, there has been a noticeable trend in the adoption of encryption strategies among businesses.
- In 2015, 37% of businesses reported implementing an overall encryption plan or strategy consistently across their entire enterprise. Meanwhile, 48% had a limited encryption plan applied to specific applications and data types, leaving 15% with no encryption strategy in place.
- Subsequently, there was a gradual increase in the adoption of consistent encryption strategies, with the percentage rising to 50% in 2020.
- Conversely, the proportion of businesses with limited encryption plans decreased steadily from 44% in 2016 to 37% in 2020.
- Notably, the percentage of businesses without any encryption plan remained relatively stable throughout the period, hovering around 13%.
Discuss your needs with our analyst
Please share your requirements with more details so our analyst can check if they can solve your problem(s)



