Table of Contents
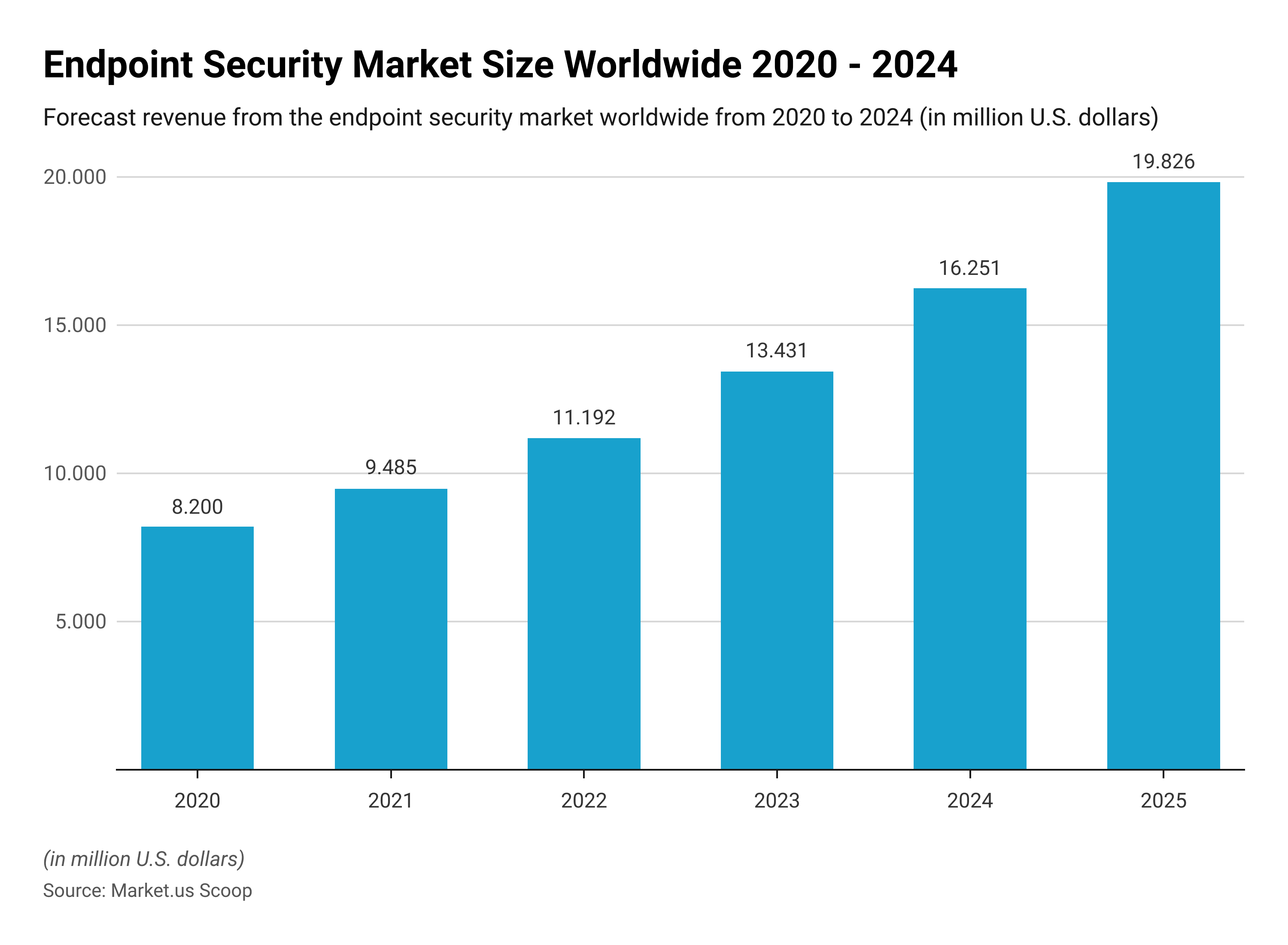
According to Endpoint Security Statistics, The global endpoint safety market is expected to reach 11 billion US dollars in 2022 and continue to expand as cyber security becomes increasingly important to enterprises today.
Endpoint Security Adoption
Endpoint security suites are increasingly being used by companies of all sizes, and across different industries. Here are some important trending areas for adoption
Small and medium-sized enterprises (SMBs) are progressively adopting endpoint security suites as they become less expensive and easy to implement.
The finance and healthcare industries are among the top adopters of endpoint security suites because of their strict security demands.
Endpoint protection software is also being adopted by government and public sector companies in an effort to protect their information and networks.
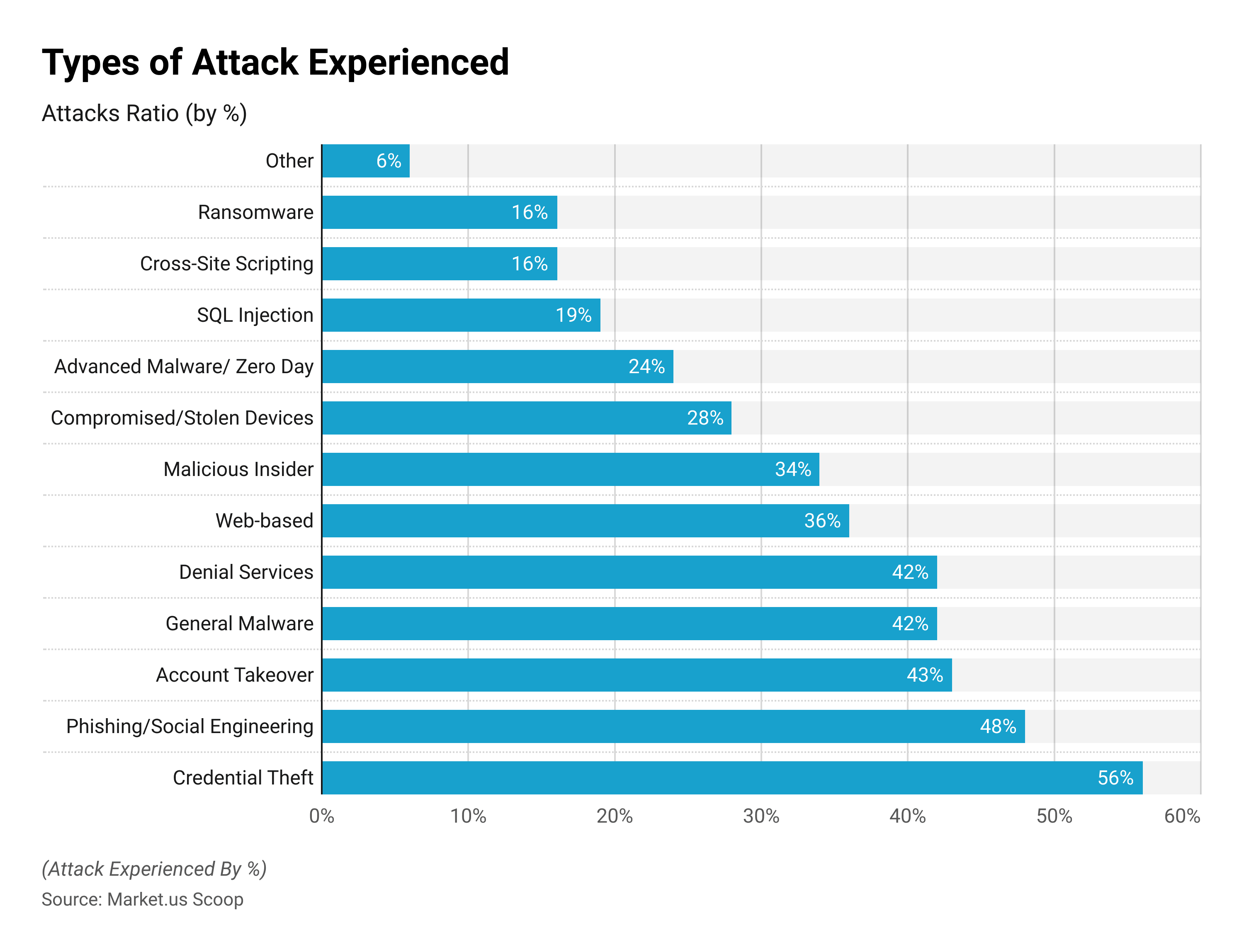
The Occurrence of Endpoint Attacks
In Ponemon Institute research, 68% of companies had experienced at least one endpoint attack that successfully hacked data or IT infrastructure. Based on the study 68% of IT experts believe that the number of attacks on endpoints has risen over the last year.
According to a separate Ponemon study, attacks on devices were among the most common attacks people have faced in the past, with 81% of businesses being hit by some form of malware, and 28% having attacks that involve stolen or hacked equipment.
Ransomware is among the most prevalent and destructive forms of malware that is currently being used. After being downloaded onto the device of the victim, the malware blocks users from accessing the company’s data or makes it encrypted until the company that is targeted pays the ransom. In 2021 53% of businesses were hit by a ransomware attack and around 23% of them experienced multiple attacks.
Unfortunately, this number shows that ransomware is currently increasing. According to a recent SonicWall analysis, the ransomware attacks in 2017 constituted an astonishing 148% percent increase year-over-year over 2020. An additional Check Point study found that the average weekly ransomware-related attacks targeting businesses were up by 50% in 2021 when compared to the year 2020.
With this in mind, there’s no reason to wonder why 60% of the CISOs are expecting at the very least one ransomware attack in 2022.
Endpoint Attack Methods
Malware is among the most widely used methods by which attackers attack endpoints and can be installed on a victim’s device in various ways.
According to Verizon reports, using password dumpers that allow attackers to take credentials on compromised devices, is the most frequent type of malware-related intrusion. It accounts for more than 40% of all attacks. The next most common type of malware is application ransomware and data capture.
Based on the study, Windows apps and Office documents are among the most popular files that contain malware. Emails and the internet are among the most popular methods for spreading viruses.
According to a Webroot study, 83% of malware-related threats are stored in four places such as %tmp percent, %appdata cache%, and the desktop.
Moreover
It is also possible to install malware through “juice Jacking,” which is the process of altering USB ports to install malware onto the device of the victim. In public areas, the ports are often disguised as charging devices for free.
This is a method to look out for in businesses that employ an abundance of remote employees or those who travel regularly as a part of their work. 79% of people who work from home have connected their devices to an open USB outlet or charger, accidentally giving a potential hacker access.
Malware, however, isn’t just a threat to your enterprise’s endpoints. “SIM switching” is a form of cybercrime where the attacker contacts the mobile phone provider of their target in a fake name and requests the victim to change their phone number to a number they have. This lets the attacker divert all calls and text messages from their intended target. Since the year 2016 switching SIM card attacks on mobile devices have increased by more than a third each year, and the amount of users using personal phones at work has risen.
Ransomware
Ransomware is among the most common types of malware. According to research by Sophos the most likely (29 percent) to be introduced into an organization through files downloaded or emails with an infected link. The phishing method is followed by remote attacks on the server, which account for 21% of ransomware attacks, and emails with malicious attachments make up 16% of attacks.
The numbers are verified by research done recently in recent times by SonicWall and SonicWall that shows that Ryuk ransomware, which is typically distributed via TrickBot and Emotet’s phishing campaigns is responsible for approximately one-third of ransomware-related attacks.
However, where do your data be after the ransomware is in place?
Well, 59% of ransomware-related attacks where data is encrypted are stored in public cloud systems like Office 365 or Amazon Web Services (AWS). This is about the location where the data was stolen from and how the attacker utilizes the data. The majority of attackers send stolen data to an authentic cloud-based storage provider, making the crime harder to trace. Google Drive, Amazon S3, and Mega. nz are the most commonly used cloud storage solutions to store data that has been stolen.
The typical data breach costs $4.27 million, according to IBM. Ransomware and malicious assaults that delete or wipe data destructively cost an average of $4.62 million and $4.69 million, respectively, while the cost of a successful endpoint attack has risen from 7.1 million to $8.94 million.
According to Coveware analysis, the average compensation of ransomware attacks remained fairly steady between Q2 and Q3 2021, however, the median reward more than doubled. This could be due to attackers avoiding larger targets, which could result in a national political or law enforcement response, and instead focusing on mid-market firms.
Top 11 Endpoint Security Solutions for Business
- ESET Endpoint Security
- Heimdal™ Threat Prevention Endpoint
- Avast Small Business Solutions
- Bitdefender GravityZone
- Trend Micro
- Crowdstrike Falcon
- Trellix Endpoint Security
- Microsoft Defender Advanced Threat Protection
- SentinelOne
- Sophos Endpoint Protection
- Symantec Endpoint Protection
Top 10 Antivirus Software for Small Businesses
- ESET Endpoint Security
- Heimdal™ Next-Gen Endpoint Antivirus
- Avast Small Business Solutions
- AVG Business
- Bitdefender GravityZone Business Security
- Norton Small Business
- Sophos Intercept X
- Trellix Endpoint Security (ENS)
- Trend Micro Worry-Free Business Security
- WithSecure Elements Endpoint Protection
Most common endpoint security threats:
- Malware: Malware is any harmful program that attempts to breach an encrypted network. It is frequently made up of embedded programs or scripts that can access the network and steal vital corporate information. Cybercriminals may employ malware to change data, steal login passwords, or hold critical data hostage.
- Ransomware: Ransomware is a virus that employs encryption to hold a victim’s data hostage in exchange for a charge. Ransomware encrypts the user’s vital data, databases, and applications and refuses to decrypt them until the victim meets the cybercriminal’s demands. It is intended to spread quickly and cripple a whole corporation.
- IoT devices The Internet-of-things also known as IoT short is a rapidly growing network of interconnected objects that communicate in real-time via embedded networks. Examples include smart lighting, smart appliances as well as thermostats for washing machines as well as a variety of smart appliances. The dishwasher of 2022 will be able to emit a tweet, but it is also a sign that it can be hacked. Despite its simplicity, IoT can play into cybercriminals’ attacks by enhancing the security of your company.
- Phishing is a type of cybercrime that uses fraud to gain usernames and passwords to access information. This is among the most frequent security threats for endpoints. Phishing scams usually are launched via email and can be extremely evident, yet they are also planned and well-planned attacks.
- Remote devices: Because of the introduction of COVID-19 in the coronavirus pandemic, numerous organizations have implemented work-from-home policies and are managing employee health care. Remote-based connections are an excellent technique for hackers to gain access, allowing them to exploit your systems for business, then your network, and finally the entire company.
Future of Endpoint Security
- More widespread adoption of Artificial Intelligence as well as Machine Learning: Artificial intelligence (AI) and machine learning (ML) technologies play an increasing role in security for endpoints. These technologies provide advanced security capabilities for detection and response to threats as well as behavioral analysis and anomaly detection. They help to detect and combat new threats in real time. AI and ML additionally enable automation as well as the capability to learn and adapt to new threats, which makes the security of endpoints more efficient and efficient.
- Endpoint Detection and Response (EDR) Integration The endpoint detection and reaction (EDR) methods are growing in recognition in cyberspace. EDR concentrates on detecting, analyzing, and combating advanced threats that evade conventional security methods. Shortly, EDR capabilities will likely be integrated into more comprehensive security solutions for the endpoint, providing companies with complete protection and visibility across their devices.
- Cloud-based Endpoint Security With the rising popularity of cloud-based services and remote workplaces cloud-based security solutions are becoming more popular. They provide central management, scalability, as well as real-time threat analysis that allow organizations to safeguard their endpoints no matter their geographical location. Cloud-based solutions also allow for quick updates and patch management to ensure that endpoints are secure against new threats.
More Insights
- Zero Trust Security: The idea of Zero Trust Security, which believes that no device or user device can be trusted automatically is growing in popularity. With Zero Trust the endpoints are constantly checked for authenticity, and access controls are continuously adjusted in response to the user’s behavior, the health of the device, and the network’s conditions. This method reduces the threat surface and also helps to prevent access by unauthorized users even when an endpoint has been compromised.
- Integration with Security Orchestration, Automation, and Response (SOAR): Endpoint security solutions are expected to be connected to Security Orchestration, Automation, and Response (SOAR) platforms. SOAR platforms offer an automated incident response as well as threat intelligence integration and simplified workflows. Through integration with SOAR security solutions for endpoints, these solutions make use of automation to swiftly respond to security threats, investigate incidents, and fix security vulnerabilities.
- The focus is on user-centric security: As the traditional security perimeter of networks becomes less clear because of the increasing use in mobile and remote working, security for endpoints will be increasingly focusing on user-centric approaches. This means securing the identity of the user and providing the security of access to resources, regardless of the device or network employed. Technologies like multi-factor authentication Secure Access Service Edge (SASE), as well as Identity and Access Management (IAM), are going to play crucial aspects in this new user-centric approach.
- Privacy and Privacy and Data Protection: Privacy regulations like the GDPR, as well as the California Consumer Privacy Act (CCPA), have highlighted the importance of safeguarding personal information. Future security solutions for endpoints will have to take into consideration privacy concerns and offer robust security measures for data. Data loss prevention, encryption, (DLP), and other privacy-focused features will become an integral part of the cybersecurity solutions for endpoints.
Discuss your needs with our analyst
Please share your requirements with more details so our analyst can check if they can solve your problem(s)



