Table of Contents
Introduction
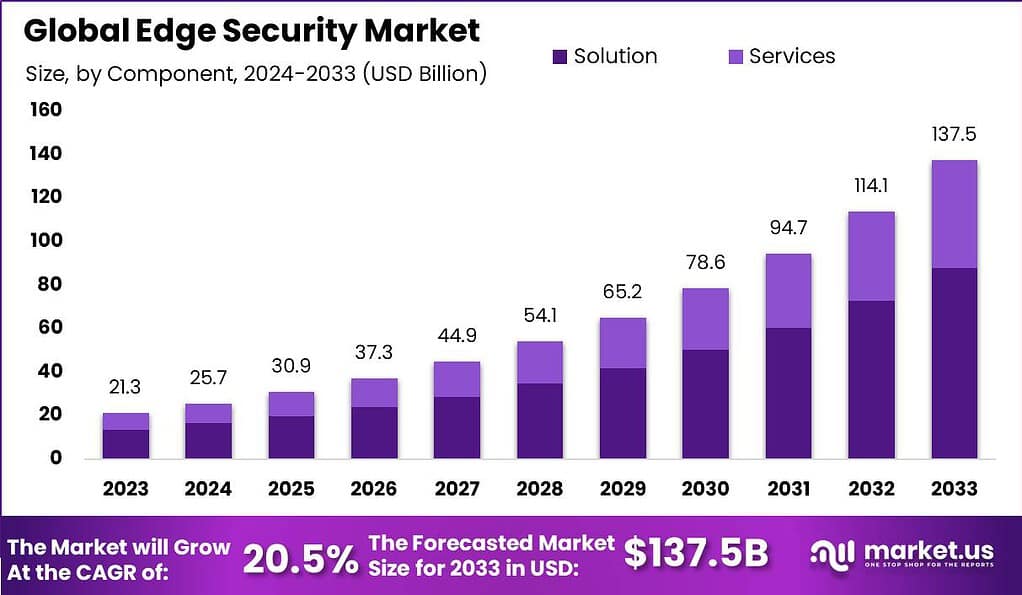
According to market.us, The Global Edge Security Market is projected to grow significantly, reaching an estimated value of USD 137.5 billion by 2033, up from USD 21.3 billion in 2023. This growth reflects a robust compound annual growth rate (CAGR) of 20.5% during the forecast period from 2024 to 2033.
The Edge Security Market is rapidly growing as businesses increasingly rely on edge computing to process data closer to where it is generated. This approach speeds up data processing and reduces latency, but it also introduces new security challenges that must be addressed to protect sensitive information and maintain system integrity.
One of the primary growth factors for the edge security market is the expansion of the Internet of Things (IoT). As more devices connect to the internet, from home appliances to industrial equipment, the need to secure data at the edge of networks becomes crucial. Additionally, the rise in remote work has pushed organizations to decentralize their data processing, further driving the demand for robust edge security solutions.
However, this market faces several challenges. The dispersed nature of edge computing makes it difficult to enforce consistent security policies and monitor all endpoints effectively. There is also the complexity of integrating edge security with existing IT infrastructure, which can be both costly and time-consuming. Despite these challenges, the edge security market presents significant opportunities. There is a growing need for innovative security solutions that can automatically detect and respond to threats at the edge.
Companies are also looking to leverage artificial intelligence and machine learning to enhance the effectiveness of their security measures. Furthermore, as regulations around data protection continue to tighten, there will be a greater demand for security solutions that can ensure compliance across different regions and industries.
Edge Security Statistics
- The Global Edge Security Market is on a significant growth trajectory, with a steady increase in market size projected over the next decade. In 2023, the market size stood at $21.3 billion. This figure is expected to rise to $25.7 billion in 2024 and continue its upward trend, reaching $30.9 billion in 2025. This growth is driven by the increasing adoption of edge computing technologies and the need for enhanced security measures to protect distributed computing environments.
- Specifically, 22% of the total investment in edge computing is allocated to security-related activities. This includes the comprehensive design, deployment, and ongoing maintenance of security infrastructures tailored to the unique challenges posed by edge environments.
- The solution segment led the market in 2023, accounting for 64% of the total market share.
- The cloud-based segment was the top performer in 2023, commanding 67.5% of the market.
- Large enterprises dominated the market in 2023, representing 68.3% of the total share.
- The IT and Telecommunications sector emerged as the leading industrial vertical in 2023, with a 25.4% market share.
- North America held the largest market share in the edge security market in 2023, with more than 36.1% of the total market.
- As the decade progresses, the market is anticipated to maintain this momentum. By 2026, the market is projected to expand to $37.3 billion, and further to $44.9 billion in 2027.
- The growth is expected to accelerate even more in the following years, with the market size forecasted to reach $54.1 billion by 2028 and $65.2 billion in 2029. The trend is expected to continue, culminating in a market size of $137.5 billion by 2033. This consistent growth reflects the increasing reliance on edge computing and the corresponding demand for robust security solutions in a rapidly digitalizing world.
- Edge computing market size is expected to be worth around USD 206 billion by 2032, growing at a CAGR of 18.3% during the forecast period from 2023 to 2032.
- The Global Multi-Access Edge Computing (MEC) Market is witnessing exponential growth, with its revenue estimated at USD 3.2 billion in 2023. This market is expected to reach a substantial USD 92.4 billion by 2032, representing a remarkable compound annual growth rate (CAGR) of 46.7% over the forecast period.
5 Top Options for Edge Security
Here are five top options for edge security, explained in straightforward terms:
- Firewalls at the Edge: Think of these as digital checkpoints that monitor and control incoming and outgoing network traffic at the boundary where your network meets the internet. They block unauthorized access and filter traffic to keep your network safe.
- Secure Access Control: This involves using strong authentication methods, like passwords, biometrics, or security keys, to verify the identity of users and devices before granting access to sensitive data or resources.
- Encryption: This converts sensitive information into a code to prevent unauthorized access. It ensures that even if data is intercepted, it remains unreadable without the correct decryption key.
- Endpoint Security: Protecting individual devices (like smartphones, laptops, or IoT devices) connected to your network. This includes installing antivirus software, keeping devices updated, and monitoring for unusual behavior.
- Edge Computing Security Solutions: Specifically designed tools and protocols to secure data and processes at the edge. These solutions often include real-time threat detection, data encryption for local processing, and secure communication between edge devices and central servers.
Edge Computing Budget to Security Measures
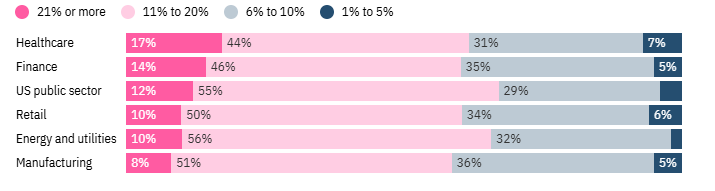
Most organizations anticipate allocating over 10% of their edge computing budget to security measures.
Source: techmonitor.ai | AT&T Cybersecurity – 2022 Securing the Edge
Emerging Trends
- AI and Machine Learning in Security: The incorporation of artificial intelligence (AI) and machine learning (ML) is revolutionizing edge security by enabling more sophisticated threat detection and response capabilities. This includes automated incident responses and predictive capabilities that identify potential threats before they manifest.
- Passwordless Authentication Systems: The shift towards passwordless authentication is gaining momentum due to its enhanced security features, such as biometric data and one-time passcodes, which provide a more secure alternative to traditional password-based systems.
- Ransomware Protection and Mitigation: With ransomware attacks becoming increasingly sophisticated, there is a heightened focus on developing robust ransomware mitigation strategies. This includes the use of advanced cloud security solutions and educational programs to prepare organizations against such threats.
- Enhanced IoT Security: With the proliferation of IoT devices, securing these devices has become a paramount concern. Managed services are evolving to offer specialized IoT security solutions that ensure regular updates, vulnerability assessments, and real-time monitoring to safeguard against the increasing risk of cyberattacks.
- Geopolitical Influences on Cybersecurity: Geopolitical conflicts are increasingly influencing cybersecurity strategies, affecting everything from the cybersecurity supply chain to the types of cyber threats organizations face. This trend emphasizes the need for a global perspective on cybersecurity practices and collaboration across borders to mitigate risks.
Top Use Cases
- Autonomous Vehicles (AV): Edge computing significantly improves traffic management and safety for AVs. By processing data locally at traffic intersections, AVs can respond more quickly to changes in traffic conditions, pedestrian movements, and other vehicles, reducing latency and enhancing safety.
- Healthcare: In medical facilities, edge computing plays a critical role by enabling real-time data analysis. This quick processing helps in monitoring patient conditions continuously, supporting remote-controlled surgeries, and ensuring data privacy and compliance with standards like HIPAA.
- Retail: Edge computing offers retailers enhanced customer experiences through faster and more personalized service. By processing data locally, stores can implement features like facial recognition and targeted advertising without compromising user privacy.
- Security Surveillance: Edge computing improves the responsiveness of security systems by processing surveillance data on the spot. This allows for immediate threat detection and alerts, which is crucial for effective security management.
- Wildfire Detection: Through edge computing, systems like Dryad’s Silvanet utilize solar-powered gas sensors within a large-scale IoT mesh network for early wildfire detection. This setup allows for the rapid processing and communication of critical data to forest managers and first responders.
Major Challenges
- Increasing Threat Landscape: As the connectivity of devices and systems expands with the Internet of Things (IoT) and other digital technologies, the threat landscape continues to grow. Attacks such as ransomware, phishing, and insider threats remain prevalent and pose significant risks to enterprises and individuals alike. The growing sophistication of cyber threats, coupled with their increasing frequency, complicates the defensive measures required at the edge.
- Deep Learning and Intrusion Detection: Deep learning techniques, such as Convolutional Neural Networks (CNNs), are being leveraged to enhance cybersecurity at the edge. These methods are effective in early detection of subtle anomalies that could indicate cyberattacks, allowing organizations to preemptively address potential security breaches. However, these technologies also require significant data and processing capabilities, which can be a challenge at the edge due to resource constraints.
- Distributed Denial of Service (DDoS) Attacks and Cyberwarfare: Edge computing is increasingly targeted by DDoS attacks and other forms of cyberwarfare. These attacks can disrupt services and cause significant damage. The edge’s role in quickly setting up defenses and managing data flows is crucial, but also presents challenges in ensuring all parts of the network can withstand and quickly recover from such attacks.
- Quantum Computing Threats: The advent of quantum computing poses new challenges for cybersecurity, particularly around encryption. Quantum computers have the potential to break existing cryptographic protocols, which would compromise the security of sensitive data. The development and implementation of post-quantum cryptography is therefore a pressing issue.
- Talent Gap and Automation: There is a significant shortage of skilled cybersecurity professionals, which is exacerbated by the rapid growth of edge computing and the complexities it introduces. Automation of cybersecurity processes at the edge is seen as a solution to manage this gap, but developing and deploying effective automated systems is itself a complex challenge that requires innovative approaches.
Top Opportunities
- Smart City Developments: Increasing investments in smart city initiatives offer significant opportunities for edge security solutions to protect interconnected urban infrastructures.
- Cloud-Based Security Solutions: There is a growing demand for cloud-based security management systems that offer centralized control over distributed edge environments.
- Advancements in AI and Machine Learning: Leveraging AI and machine learning for real-time threat detection and response at the edge presents substantial market opportunities.
- Zero Trust Architectures: Implementing Zero Trust architectures that require all users, whether in or outside the network, to be authenticated, authorized, and continuously validated for security configuration and posture before being granted or keeping access to applications and data.
- Regulatory Compliance: Increasing regulatory requirements around data privacy and security are driving the need for compliant edge security solutions, opening new avenues for growth.
Recent Developments
Cisco Systems, Inc.
Cisco has been actively enhancing its edge security offerings to address the increasing threats at the network edge. In 2024, Cisco introduced new capabilities within its Secure Firewall 3100 Series, specifically designed to support the hybrid work environment, which has become prevalent. These firewalls are equipped to handle more remote users and improve VPN performance significantly. Moreover, Cisco has been pushing its Zero Trust architecture with Duo Passwordless Authentication to reduce reliance on traditional passwords, enhancing security at the user level. Cisco’s Security Cloud, which integrates multiple security solutions including Secure Access Service Edge (SASE), is central to their strategy, ensuring seamless protection across public and private cloud environments.
Palo Alto Networks Inc.
Palo Alto Networks continues to strengthen its edge security portfolio through its Prisma Access platform, which is a leading SASE solution. In 2023, the company expanded its AI-powered security capabilities to offer more precise threat detection and response. Prisma Access integrates Zero Trust principles, providing robust protection for remote and hybrid workforces by securing both users and applications across different cloud environments. The platform’s ability to provide secure, scalable, and consistent security services makes it a critical asset in the fight against edge-based cyber threats.
Fortinet Inc.
Fortinet has made significant advancements in edge security by enhancing its FortiSASE solution. The company added new cloud-delivered security features in 2023, aimed at providing comprehensive protection for remote users and securing access to cloud and SaaS applications. Fortinet’s focus on delivering a unified security fabric that integrates network and security functionalities allows for improved threat visibility and control, which is crucial in managing the complexities of edge environments.
Check Point Software Technologies Ltd.:
Check Point has been focusing on securing the edge with its Infinity architecture, which consolidates threat prevention capabilities into a single platform. In 2023, the company launched new features in its Harmony and Quantum security suites, designed to provide end-to-end protection against sophisticated attacks targeting remote workers and edge devices. The emphasis on real-time threat intelligence and automated response mechanisms helps organizations secure their increasingly dispersed networks.
Broadcom Inc.
Broadcom has been integrating its Symantec enterprise security solutions with edge computing frameworks to enhance protection at the network boundary. In 2023, Broadcom emphasized securing workloads across hybrid and multi-cloud environments by leveraging AI and machine learning to detect and mitigate threats at the edge. Their advanced threat protection systems are designed to safeguard critical data as it moves closer to the edge, particularly in industries like finance and healthcare.
McAfee LLC
McAfee has been expanding its edge security capabilities by focusing on cloud-native solutions that protect data and applications at the edge. In 2023, the company enhanced its Cloud Access Security Broker (CASB) and Secure Web Gateway (SWG) offerings, providing stronger security controls for organizations transitioning to edge computing. McAfee’s solutions are designed to enforce consistent security policies across all edge endpoints, ensuring robust protection against emerging threats.
Zscaler Inc.
Zscaler remains a leader in the SASE space, with a strong focus on securing the edge. The company’s cloud-native architecture provides secure access to applications regardless of the user’s location, making it ideal for the distributed workforce. In 2023, Zscaler introduced new AI-driven features to its Zero Trust Exchange platform, which enhances security by ensuring that only authorized users and devices can access sensitive resources at the edge.
F5 Inc.
F5 has been integrating its application security solutions with edge computing environments to enhance the protection of applications and APIs. In 2023, F5 launched new capabilities within its Distributed Cloud Services, which are designed to secure applications closer to where they are consumed – at the edge. The emphasis on securing application delivery and performance while reducing latency makes F5 a key player in the edge security market.
Juniper Networks Inc.
Juniper Networks has been strengthening its edge security portfolio by incorporating AI-driven insights into its Secure Access Service Edge (SASE) solutions. In 2023, Juniper launched enhancements to its AI-powered threat detection capabilities, allowing for more proactive security measures at the edge. These solutions are designed to support the growing demands of IoT and 5G networks, ensuring robust protection across increasingly complex edge environments.
Akamai Technologies Inc.
Akamai continues to lead in the edge security market by focusing on protecting web applications and content delivery networks (CDNs). In 2023, Akamai introduced enhancements to its Web Application and API Protection (WAAP) solutions, providing stronger defenses against DDoS attacks and other threats targeting the edge. Akamai’s edge security solutions are essential for organizations looking to secure their digital assets as they expand their presence at the network edge.
Forcepoint
Forcepoint has been focusing on behavioral analytics to enhance its edge security offerings. In 2023, the company expanded its Data Loss Prevention (DLP) and Cloud Access Security Broker (CASB) solutions to better secure data at the edge. Forcepoint’s approach to combining human-centric security with advanced analytics enables organizations to detect and respond to threats in real-time, providing critical protection for edge environments.
Conclusion
In conclusion, the edge security market is poised for substantial growth as organizations increasingly embrace edge computing to meet the demands of modern data processing. The proliferation of IoT devices and the shift towards remote work environments underscore the critical need for robust security measures at the edge of networks. While the market faces challenges related to the complexity of managing dispersed systems and integrating new solutions with existing infrastructures, the opportunities are significant.
Advancements in AI and machine learning, coupled with the growing regulatory landscape, will drive the development and adoption of innovative security solutions that can proactively address emerging threats and ensure compliance. As businesses continue to decentralize their data operations, the role of edge security will only become more pivotal in safeguarding sensitive information and maintaining system integrity.


